Roles and Security Settings
Overview
The Roles and Security Settings of your SmartSimple instance can be accessed through the following steps:
1. Click the 9-square menu icon on the top right of your page.
2. Under the heading Configuration, select Roles and Security Settings.
The Roles and Security Settings page will be displayed.
Access
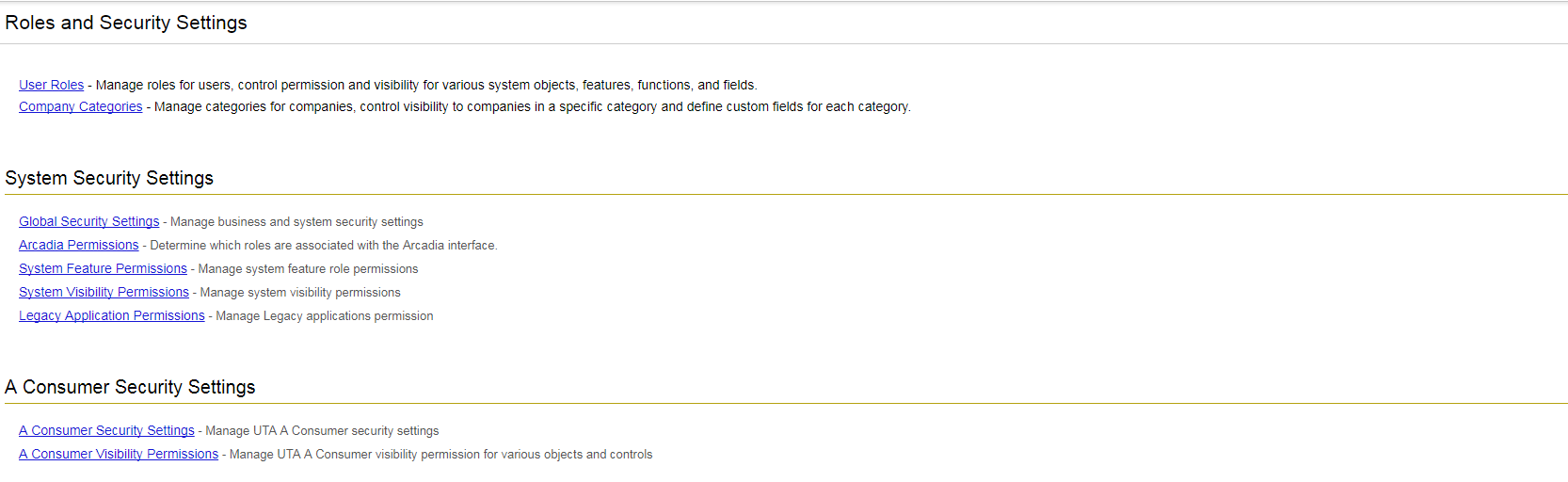
This page allows access to the following configuration pages within SmartSimple:
| Roles and Categories |
User Roles - Use roles in order to control the menu, portal, reports, and fields associated with a specific group of users or contacts. Roles also control field visibility and the types of contacts that a user in a specific role is able to add into the system. It is under this tab that you are also able to edit the Common Portal, the aggregated portal that can be helpfully applied to users in all roles rather than a specific role.
|
| System Security Settings |
Global Security Settings - Arcadia Permissions - System Feature Permissions - System Visibility Permissions - Legacy Application Permissions - |
| -based Settings |
UTA Security Settings - UTA Visibility Settings - |
- Role and Security Settings
- User Roles - Use roles to control the menu, portal, reports and fields associated with a specific group of users or contacts. Roles also control field visibility and the types of contacts a user in a specific role can add to the system.
- Organization Categories - Use this feature to create categories for companies, control visibility to companies in a specific category and define custom fields for each category.
- Permission Settings
- Global Security Settings - Manage business and system security settings.
- Arcadia Permissions - Determine which roles are associated with the Arcadia interface.
- System Feature Permissions - Allows for system administrators to personalize their copy of SmartSimple and to make various system objects available to users in different roles.
- System Visibility Permissions - Allows for system administrators to personalize their copy of SmartSimple and to make various system objects available to users in different roles.
- Legacy Application Permissions - Determine which roles are associated with base application functions.
- UTA Settings
- UTA Security Permissions - Security settings of the UTA.
- UTA Visibility Permissions - Determine visibility permission for various objects and control