Difference between revisions of "Password Policy"
| Line 4: | Line 4: | ||
==Overview== | ==Overview== | ||
| + | '''Password Policy''' is used to configure the Password Policies within SmartSimple with your organizational policies. It is best practice to ensure that these policies match the other systems that are deployed by your organization. Consequently these policies provide for extensive configuration options. | ||
| − | + | Password Policies include the ability to control; the length and complexity of passwords, password expiration and frequency usage, the method for sending new requested passwords, word restrictions, the number of retries allowed, the lockout time for the account if they exceed the number of retries, email alerts for invalid passwords. | |
| − | + | '''Multiple password policies''' can be supported by the system. This feature provides for less stringent policies for types of users that infrequently access the system such as external contacts. Alternative password policies can be set for any level in the organizational hierarchy. | |
| − | + | There can also be individual Password policies for the different a company in your organizations hierarchy. However, they will only be able to edit the policy and not the Activation Emails. These emails can only be configured from [[Global Settings|Global settings]]. | |
| − | |||
==Settings== | ==Settings== | ||
| − | |||
===Password Encryption=== | ===Password Encryption=== | ||
{{PasswordEncryption}} | {{PasswordEncryption}} | ||
| + | |||
===Persistent Login and Expiration of Inactive Accounts=== | ===Persistent Login and Expiration of Inactive Accounts=== | ||
| + | [[image:password001.png|border]] | ||
| − | + | '''Persistent Login''' provides for the use use of a persistent secure cookie on the users computer to eliminate the need to use a username and password to log into the system. '''This feature will be deprecated in the July 2016 upgrade.''' | |
| + | '''Disable Inactive Accounts''' provides the ability to automatically disable a user account after a predetermined period of time. A password reset is required by the user to regain access to the system. The main options are: | ||
| − | + | * '''Disable user accounts after ''[X]'' days''' - The number of days a user account is inactive before it is disabled. Leave this field blank to disable this feature. | |
| − | |||
| − | * '''Disable user accounts after ''[X]'' days''' - The number of days a user account is inactive before it is disabled. | ||
* '''Apply Policy to All Sub-Companies''' - Click button to force-update the password policy of the current company and all sub-companies. '''Note:'''This is applicable when an organization has a root company and a one or more sub-companies each with it's own password policies. | * '''Apply Policy to All Sub-Companies''' - Click button to force-update the password policy of the current company and all sub-companies. '''Note:'''This is applicable when an organization has a root company and a one or more sub-companies each with it's own password policies. | ||
* '''Disabled Inactive Account Message''' - The text to be displayed to a user trying to access an expired account. | * '''Disabled Inactive Account Message''' - The text to be displayed to a user trying to access an expired account. | ||
===Password Settings Section=== | ===Password Settings Section=== | ||
| − | |||
This section is used to set password attributes | This section is used to set password attributes | ||
| Line 40: | Line 39: | ||
'''Password length''' – the minimum length allowed for a [[Password|password]], between '''6 and 32 characters'''. | '''Password length''' – the minimum length allowed for a [[Password|password]], between '''6 and 32 characters'''. | ||
| − | '''Data Restrictions''' - passwords set by users can be restricted so values such as first name, last name or organization name cannot be used in the password. | + | '''Data Restrictions''' - passwords set by users can be restricted so values such as first name, last name or organization name cannot be used in the password. Any number of fields can be selected from both the organization or the user profile; standard and custom fields are supported. |
[[image:password-008.png]] | [[image:password-008.png]] | ||
In the example above City, Country and Phone fields have been selected from the user's organization record and first name, last name, birthplace and nickname fields have been selected from the user profile. | In the example above City, Country and Phone fields have been selected from the user's organization record and first name, last name, birthplace and nickname fields have been selected from the user profile. | ||
| + | |||
====Password Complexity==== | ====Password Complexity==== | ||
| + | '''Complexity''' – the level of complexity required in the [[Password|password]], the options are: | ||
| − | + | * '''No Restriction''' – any character can be used. This is the default. | |
| − | * '''No Restriction''' – any character can be used. | ||
* '''Alpha Only''' – only letters can be used. | * '''Alpha Only''' – only letters can be used. | ||
* '''Alpha & Numeric''' – letters and numbers must be used in the password. | * '''Alpha & Numeric''' – letters and numbers must be used in the password. | ||
| Line 57: | Line 57: | ||
====Custom Policy==== | ====Custom Policy==== | ||
| − | + | * The '''Compose Custom Password Policy''' table provides the ability to define the custom password policy that matches your organization's security standards and provides control of each character type desired (upper case, lower case, numeric and/or symbols). You can also specify the minimum number of characters required for that character type. | |
| − | * The '''Compose Custom Password Policy''' table provides the ability to define the custom password policy that matches your organization's security standards and provides control of each character type desired (upper case, lower case, numeric and/or symbols). | ||
* The character mask used to define your selection will appear in the '''Custom Password Policy''' field. You can also write your own code and paste it into this field if desired. | * The character mask used to define your selection will appear in the '''Custom Password Policy''' field. You can also write your own code and paste it into this field if desired. | ||
| − | * The '''Validate Pattern''' button will open a window where you can test various passwords against the policy to see if they will pass or fail. | + | * The '''Validate Pattern''' button will open a window where you can test various passwords against the policy to see if they will pass or fail. |
* The value in the '''Custom Password Policy Description''' field will be displayed to users when setting/changing their password. You can use plain text or html in this field (For example, to insert a line break use ''<br>'') | * The value in the '''Custom Password Policy Description''' field will be displayed to users when setting/changing their password. You can use plain text or html in this field (For example, to insert a line break use ''<br>'') | ||
* '''Note''': See also [[Custom Password Policy Examples]] | * '''Note''': See also [[Custom Password Policy Examples]] | ||
| Line 68: | Line 67: | ||
If you need to translate the '''Custom Password Policy Description''' message you can use [[sslogic]]. It is often easiest to use [[System Variables]] for these. Example: | If you need to translate the '''Custom Password Policy Description''' message you can use [[sslogic]]. It is often easiest to use [[System Variables]] for these. Example: | ||
| − | <pre style=" | + | |
| − | + | <pre style="white-space: -o-pre-wrap; word-wrap: break-word;"><!--@sslogic('@langid@'='2')--><br>@system.Password Policy - French@<!--@else--><br>@system.Password Policy@<!--@end--></pre> | |
| − | |||
| − | |||
| − | |||
===New Password Settings=== | ===New Password Settings=== | ||
| + | [[image:password003.png|border]] | ||
| − | + | * '''Force Password Change''' - Appears with button marked '''Expire All Passwords Now'''. Ensures that all users will be forced to rest their password when they next log in. | |
| − | |||
| − | |||
* '''First Login''' - Ensures that the user selects a password of their own choosing the first time they log into [[SmartSimple]]. <br />''(Does not count towards'' Maximum Password Update in 24 Hours ''setting.)'' | * '''First Login''' - Ensures that the user selects a password of their own choosing the first time they log into [[SmartSimple]]. <br />''(Does not count towards'' Maximum Password Update in 24 Hours ''setting.)'' | ||
| Line 86: | Line 81: | ||
* '''Password History Check''' - You can set the number of previous passwords (to a maximum of 32) that the system will remember for each user. When changing their password, users will not be permitted to re-use a previous password until the specified number of unique passwords have been used. | * '''Password History Check''' - You can set the number of previous passwords (to a maximum of 32) that the system will remember for each user. When changing their password, users will not be permitted to re-use a previous password until the specified number of unique passwords have been used. | ||
| + | |||
===Password Activation Settings=== | ===Password Activation Settings=== | ||
| − | |||
Password Activation Settings can be set to add an extra layer of security to the system. These settings pertain to users who use the "Forgot Password" link on the login page. | Password Activation Settings can be set to add an extra layer of security to the system. These settings pertain to users who use the "Forgot Password" link on the login page. | ||
[[Image:Password-Activation-Settings.png]] | [[Image:Password-Activation-Settings.png]] | ||
| − | * '''Default Security Code''' - A hard-coded value to be entered when users request new passwords. | + | * '''Default Security Code''' - A hard-coded value to be entered when users request new passwords. |
| − | * '''Activation link life span''' - Works with the @activationlink@ [[Password Variables to Set or Reset User Passwords|password variable]]. If the '''<nowiki> | + | * '''Activation link life span''' - Works with the @activationlink@ [[Password Variables to Set or Reset User Passwords|password variable]]. If the '''<nowiki>https://@url@@activationlink@</nowiki>''' syntax is used in the ''Request Password'' section of [[User Email Templates]], this setting sets the duration that the activation link will be valid. |
* '''Challenge Questions, delimited by semi-colons''' - You can set a series of challenge questions, all users will be prompted to select a [[Challenge Question]] on next login. Their answer will be stored and they will be prompted to enter this answer if they forget their password and click the activation link in the "Forgot password" email template. | * '''Challenge Questions, delimited by semi-colons''' - You can set a series of challenge questions, all users will be prompted to select a [[Challenge Question]] on next login. Their answer will be stored and they will be prompted to enter this answer if they forget their password and click the activation link in the "Forgot password" email template. | ||
| − | :[[Image:Challenge-question.png|link=]] | + | : [[Image:Challenge-question.png|link=]] |
| − | + | : '''Note:''' An example of a good challenge question would be something that is simple, memorable, can't be guessed easily, and won't change over time. | |
| − | :'''Note:''' An example of a good challenge question would be something that is simple, memorable, can't be guessed easily, and won't change over time. | ||
| − | |||
===Rules for Password Activation Settings=== | ===Rules for Password Activation Settings=== | ||
The following rules apply to the above settings when users request new passwords: | The following rules apply to the above settings when users request new passwords: | ||
| + | |||
* If a default security code has been entered and no challenge questions have been entered, the user will be prompted to enter the default security code. | * If a default security code has been entered and no challenge questions have been entered, the user will be prompted to enter the default security code. | ||
* If a default security code has been entered and challenge questions have been entered, the user will only be prompted to answer a challenge question. | * If a default security code has been entered and challenge questions have been entered, the user will only be prompted to answer a challenge question. | ||
| Line 112: | Line 106: | ||
After successful completion of Password Activation, the user will be logged in and their new password will be active. | After successful completion of Password Activation, the user will be logged in and their new password will be active. | ||
| + | |||
===Intruder Lockout Settings=== | ===Intruder Lockout Settings=== | ||
| − | |||
[[image:password-006.png]] | [[image:password-006.png]] | ||
These settings determine the actions that should be taken if someone attempts to log into your copy of [[SmartSimple]]. | These settings determine the actions that should be taken if someone attempts to log into your copy of [[SmartSimple]]. | ||
| + | |||
* '''Number of Attempts''' – the number of attempts to log in with an account before the account is locked. | * '''Number of Attempts''' – the number of attempts to log in with an account before the account is locked. | ||
| − | * '''Lockout Duration''' – the duration of the account lockout. | + | * '''Lockout Duration''' – the duration of the account lockout. The [[User|user]] will not be able to log in during this period. Period can be set to 5 minutes, 15 minutes, 30 minutes, 1 hour, 3 hours, 12 hours, 24 hours or forever (until unlocked by [[Administrator|administrator]]). |
| − | * '''Lockout Message''' - a custom message to display to users when a user is locked out due to too many failed login attempts. This message will only display when a user has been locked out, and | + | * '''Lockout Message''' - a custom message to display to users when a user is locked out due to too many failed login attempts. This message will only display when a user has been locked out, and attempts to log in again with the correct password. Therefore, no information will be divulged to users that fail their login. |
| − | * The '''View Locked Users''' tab will display all [[User|users]] that have had their account locked. | + | * The '''View Locked Users''' tab will display all [[User|users]] that have had their account locked. |
* If a user is locked, you can click on the '''Set Password''' button on the '''View Locked Users''' tab to reactivate the account and send the [[User|user]] a new [[Password|password]]. | * If a user is locked, you can click on the '''Set Password''' button on the '''View Locked Users''' tab to reactivate the account and send the [[User|user]] a new [[Password|password]]. | ||
| + | |||
| Line 135: | Line 131: | ||
===Password Reset Message=== | ===Password Reset Message=== | ||
| − | |||
[[image:password-005.png]] | [[image:password-005.png]] | ||
This feature provides the ability to overwrite the standard Password Reset message with a custom message for your organization. | This feature provides the ability to overwrite the standard Password Reset message with a custom message for your organization. | ||
| + | |||
===Intruder Email Alert=== | ===Intruder Email Alert=== | ||
| − | + | These settings define who should be informed by email if an intruder alert is detected. A default emial template is used and contains the following values: | |
| − | These settings define who should be informed by email if an intruder alert is detected. | ||
[[File:10-12-2016 1-15-24 PM.png]] | [[File:10-12-2016 1-15-24 PM.png]] | ||
| Line 152: | Line 147: | ||
You can save the default template and then modify ifrequired. | You can save the default template and then modify ifrequired. | ||
| − | * '''Email From''' – the “from” address for the email. | + | * '''Email From''' – the “from” address for the email. If you do not set this value, the address: '''donotreply@smartsimple.com''' will be used. |
* '''Email To''' – select the [[Internal|internal]] people to receive the email. | * '''Email To''' – select the [[Internal|internal]] people to receive the email. | ||
* '''Subject''' – the subject of the email. See below for the variables that you can use in the subject. | * '''Subject''' – the subject of the email. See below for the variables that you can use in the subject. | ||
| Line 158: | Line 153: | ||
'''Intruder Alert Email Variables''' – because the [[User|user]] is not logged into the system, the amount of information available is limited to IP Address '''@ip@''', the attempted username '''@username@''' and date/time '''@now@''' of the attempted login. | '''Intruder Alert Email Variables''' – because the [[User|user]] is not logged into the system, the amount of information available is limited to IP Address '''@ip@''', the attempted username '''@username@''' and date/time '''@now@''' of the attempted login. | ||
| + | |||
===Intruder Log=== | ===Intruder Log=== | ||
| − | |||
The '''View Log''' tab is used to access the '''Intruder Alert''' log. | The '''View Log''' tab is used to access the '''Intruder Alert''' log. | ||
| Line 171: | Line 166: | ||
===Hierarchical Password Policy=== | ===Hierarchical Password Policy=== | ||
| − | |||
When viewing a company in your hierarchy, select '''Settings > Password Policy''' to define. <br/><br/> | When viewing a company in your hierarchy, select '''Settings > Password Policy''' to define. <br/><br/> | ||
| Line 178: | Line 172: | ||
If there are password policies defined for a company then it will automatically apply to all sub-companies in the [[Creating_an_Organization_Chart_and_Company_Hierarchy|hierarchy]], unless those sub-companies have defined their own password policy. <br/><br/> | If there are password policies defined for a company then it will automatically apply to all sub-companies in the [[Creating_an_Organization_Chart_and_Company_Hierarchy|hierarchy]], unless those sub-companies have defined their own password policy. <br/><br/> | ||
| − | If there are no password policies defined for a company, then the system will look at the companies above it in the hierarchy, and if one of these parent companies have a password policy set then it will use these settings. | + | If there are no password policies defined for a company, then the system will look at the companies above it in the hierarchy, and if one of these parent companies have a password policy set then it will use these settings. <br/><br/> |
If there are no password policies defined for a company, or any of the companies above it in the hierarchy, then the password policy set in [[Global_Settings|Global Settings]] will apply.<br/><br/> | If there are no password policies defined for a company, or any of the companies above it in the hierarchy, then the password policy set in [[Global_Settings|Global Settings]] will apply.<br/><br/> | ||
''NOTE:'' There are no settings stored in the database for a company until someone actually opens the Password Policy page for that company and clicks Save. | ''NOTE:'' There are no settings stored in the database for a company until someone actually opens the Password Policy page for that company and clicks Save. | ||
| + | |||
==View Locked Users== | ==View Locked Users== | ||
| + | This option is only available from the Password Policy on the [[Category:Global Settings|Global settings]]. It cannot be accessed for the individual Password policies for the different companies in your organizations hierarchy. | ||
| − | + | [[Image:ViewLockedUsers.png|1000px]] | |
| − | [[ | + | The '''View Locked Users''' tab will display all [[User|users]] that have had their account locked. |
| − | |||
* Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked. | * Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked. | ||
| − | * When an account has been locked for exceeding the alloted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevent would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed. | + | * When an account has been locked for exceeding the alloted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevent would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed. |
* If a user is locked, you can click on the '''Set Password''' button to reactivate the account and send the [[User|user]] a new [[Password|password]]. | * If a user is locked, you can click on the '''Set Password''' button to reactivate the account and send the [[User|user]] a new [[Password|password]]. | ||
| + | |||
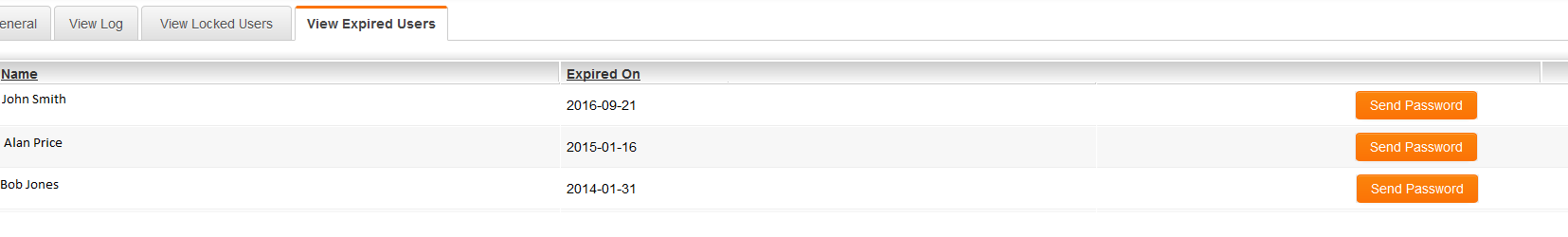
==View Expired Users== | ==View Expired Users== | ||
| − | + | This option is only available from the Password Policy on the [[Category:Global Settings|Global settings]]. It can not be accessed for the individual Password policies for the different companies in your organizations hierarchy. | |
| − | This option is only available from the Password Policy on the [[Category:Global Settings|Global settings]]. It can not be accessed for the individual Password policies for the different companies in your organizations hierarchy. | ||
[[Image:ViewExpiredUsers.png|1000px]] | [[Image:ViewExpiredUsers.png|1000px]] | ||
| − | * The '''View Expired Users''' tab will display all [[User|users]] that had their accounts disabled due to [[Password_Policy#Section_1:_Persistent_Login_and_Expiration_of_Inactive_Accounts|inactivity]]. There will be page navigation options if there is an overly long list. | + | * The '''View Expired Users''' tab will display all [[User|users]] that had their accounts disabled due to [[Password_Policy#Section_1:_Persistent_Login_and_Expiration_of_Inactive_Accounts|inactivity]]. There will be page navigation options if there is an overly long list. |
* Once an account has been expired for having been inactive for longer that the permitted number of days it will remain on the "expired users" list until their password is reset. This allows the administrator to see which users have been expired. | * Once an account has been expired for having been inactive for longer that the permitted number of days it will remain on the "expired users" list until their password is reset. This allows the administrator to see which users have been expired. | ||
Revision as of 14:02, 6 October 2017
Contents
- 1 Overview
- 2 Settings
- 2.1 Password Encryption
- 2.2 Persistent Login and Expiration of Inactive Accounts
- 2.3 Password Settings Section
- 2.4 New Password Settings
- 2.5 Password Activation Settings
- 2.6 Rules for Password Activation Settings
- 2.7 Intruder Lockout Settings
- 2.8 Password Reset Message
- 2.9 Intruder Email Alert
- 2.10 Intruder Log
- 2.11 Hierarchical Password Policy
- 3 View Locked Users
- 4 View Expired Users
- 5 Single Sign-On
- 6 See Also
Overview
Password Policy is used to configure the Password Policies within SmartSimple with your organizational policies. It is best practice to ensure that these policies match the other systems that are deployed by your organization. Consequently these policies provide for extensive configuration options.
Password Policies include the ability to control; the length and complexity of passwords, password expiration and frequency usage, the method for sending new requested passwords, word restrictions, the number of retries allowed, the lockout time for the account if they exceed the number of retries, email alerts for invalid passwords.
Multiple password policies can be supported by the system. This feature provides for less stringent policies for types of users that infrequently access the system such as external contacts. Alternative password policies can be set for any level in the organizational hierarchy.
There can also be individual Password policies for the different a company in your organizations hierarchy. However, they will only be able to edit the policy and not the Activation Emails. These emails can only be configured from Global settings.
Settings
Password Encryption
SmartSimple uses the SHA-256 algorithm, combined with salt hashing, in order to encrypt passwords.
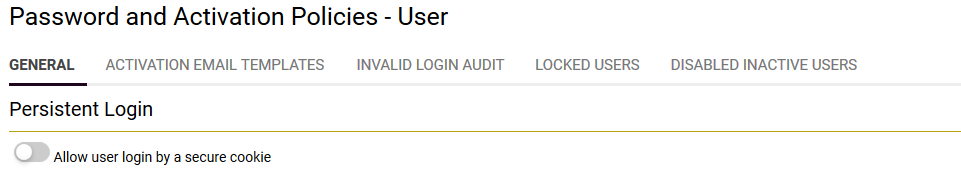
Persistent Login and Expiration of Inactive Accounts
Persistent Login provides for the use use of a persistent secure cookie on the users computer to eliminate the need to use a username and password to log into the system. This feature will be deprecated in the July 2016 upgrade. Disable Inactive Accounts provides the ability to automatically disable a user account after a predetermined period of time. A password reset is required by the user to regain access to the system. The main options are:
- Disable user accounts after [X] days - The number of days a user account is inactive before it is disabled. Leave this field blank to disable this feature.
- Apply Policy to All Sub-Companies - Click button to force-update the password policy of the current company and all sub-companies. Note:This is applicable when an organization has a root company and a one or more sub-companies each with it's own password policies.
- Disabled Inactive Account Message - The text to be displayed to a user trying to access an expired account.
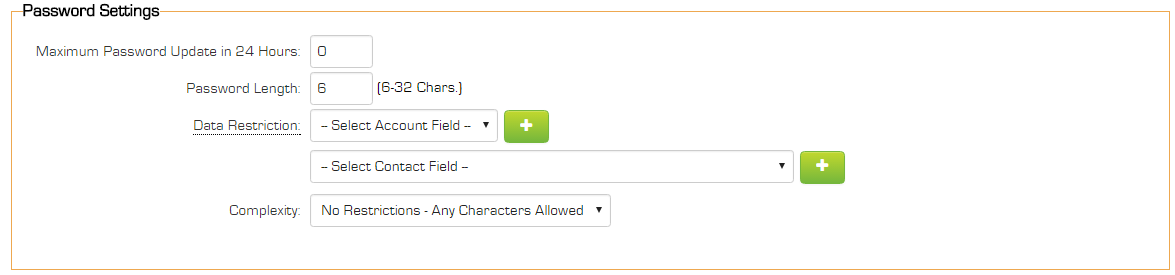
Password Settings Section
This section is used to set password attributes
Maximum Password Update in 24 Hours – Sets the maximum number of password changes a user can make within a 24 hour period can be defined. This is to prevent users bypassing the password history restriction by changing their password repeatedly to return to a previously used password. This setting only pertains to password changes by use of "Update Password" by user, not to the "Forgot Password" link or system administrators using "Set Password."
Password length – the minimum length allowed for a password, between 6 and 32 characters.
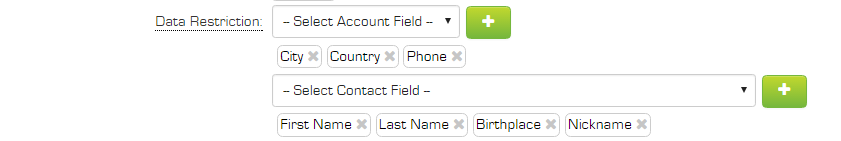
Data Restrictions - passwords set by users can be restricted so values such as first name, last name or organization name cannot be used in the password. Any number of fields can be selected from both the organization or the user profile; standard and custom fields are supported.
In the example above City, Country and Phone fields have been selected from the user's organization record and first name, last name, birthplace and nickname fields have been selected from the user profile.
Password Complexity
Complexity – the level of complexity required in the password, the options are:
- No Restriction – any character can be used. This is the default.
- Alpha Only – only letters can be used.
- Alpha & Numeric – letters and numbers must be used in the password.
- Alpha & Numeric & Special characters – letters, numbers and special characters must be used.
- Custom Policy - a password policy can be custom defined.
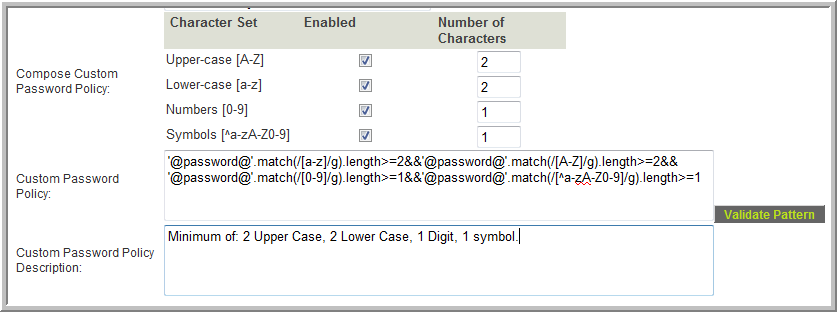
Custom Policy
- The Compose Custom Password Policy table provides the ability to define the custom password policy that matches your organization's security standards and provides control of each character type desired (upper case, lower case, numeric and/or symbols). You can also specify the minimum number of characters required for that character type.
- The character mask used to define your selection will appear in the Custom Password Policy field. You can also write your own code and paste it into this field if desired.
- The Validate Pattern button will open a window where you can test various passwords against the policy to see if they will pass or fail.
- The value in the Custom Password Policy Description field will be displayed to users when setting/changing their password. You can use plain text or html in this field (For example, to insert a line break use <br>)
- Note: See also Custom Password Policy Examples
Important: When defining a custom password policy be sure to provide a detailed description of the policy in the Custom Password Policy Description field so that users are aware of the minimum requirement to enable them to create a valid password.
If you need to translate the Custom Password Policy Description message you can use sslogic. It is often easiest to use System Variables for these. Example:
<!--@sslogic('@langid@'='2')--><br>@system.Password Policy - French@<!--@else--><br>@system.Password Policy@<!--@end-->
New Password Settings
- Force Password Change - Appears with button marked Expire All Passwords Now. Ensures that all users will be forced to rest their password when they next log in.
- First Login - Ensures that the user selects a password of their own choosing the first time they log into SmartSimple.
(Does not count towards Maximum Password Update in 24 Hours setting.)
- Password Expiration - Each user will be forced to change their password once the selected number of days has passed. Any number of days can be set.
- Password History Check - You can set the number of previous passwords (to a maximum of 32) that the system will remember for each user. When changing their password, users will not be permitted to re-use a previous password until the specified number of unique passwords have been used.
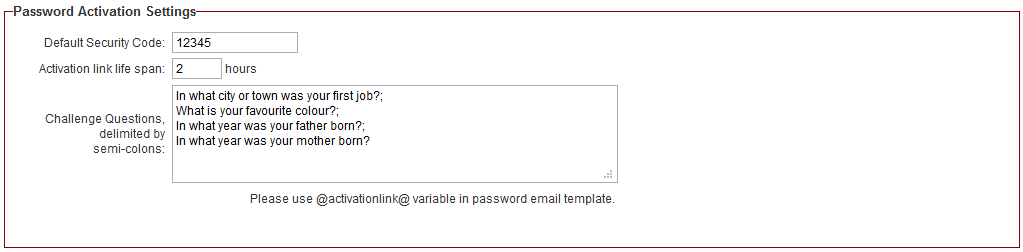
Password Activation Settings
Password Activation Settings can be set to add an extra layer of security to the system. These settings pertain to users who use the "Forgot Password" link on the login page.
- Default Security Code - A hard-coded value to be entered when users request new passwords.
- Activation link life span - Works with the @activationlink@ password variable. If the https://@url@@activationlink@ syntax is used in the Request Password section of User Email Templates, this setting sets the duration that the activation link will be valid.
- Challenge Questions, delimited by semi-colons - You can set a series of challenge questions, all users will be prompted to select a Challenge Question on next login. Their answer will be stored and they will be prompted to enter this answer if they forget their password and click the activation link in the "Forgot password" email template.
-
- Note: An example of a good challenge question would be something that is simple, memorable, can't be guessed easily, and won't change over time.
Rules for Password Activation Settings
The following rules apply to the above settings when users request new passwords:
- If a default security code has been entered and no challenge questions have been entered, the user will be prompted to enter the default security code.
- If a default security code has been entered and challenge questions have been entered, the user will only be prompted to answer a challenge question.
- The user will be presented with CAPTCHA validation in all cases.
After successful completion of Password Activation, the user will be logged in and their new password will be active.
Intruder Lockout Settings
These settings determine the actions that should be taken if someone attempts to log into your copy of SmartSimple.
- Number of Attempts – the number of attempts to log in with an account before the account is locked.
- Lockout Duration – the duration of the account lockout. The user will not be able to log in during this period. Period can be set to 5 minutes, 15 minutes, 30 minutes, 1 hour, 3 hours, 12 hours, 24 hours or forever (until unlocked by administrator).
- Lockout Message - a custom message to display to users when a user is locked out due to too many failed login attempts. This message will only display when a user has been locked out, and attempts to log in again with the correct password. Therefore, no information will be divulged to users that fail their login.
- The View Locked Users tab will display all users that have had their account locked.
- If a user is locked, you can click on the Set Password button on the View Locked Users tab to reactivate the account and send the user a new password.
- Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked.
- When an account has been locked for exceeding the allotted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevents would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed.
Password Reset Message
This feature provides the ability to overwrite the standard Password Reset message with a custom message for your organization.
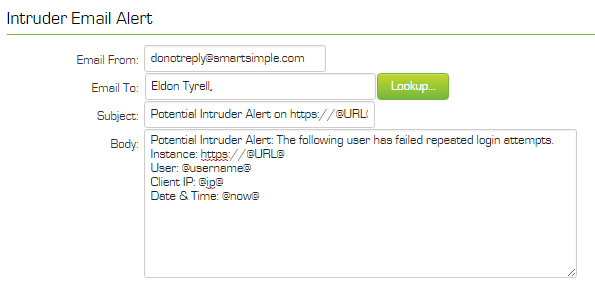
Intruder Email Alert
These settings define who should be informed by email if an intruder alert is detected. A default emial template is used and contains the following values:
The Default template uses the primary contact on the root company record to populate the Email To.
You can save the default template and then modify ifrequired.
- Email From – the “from” address for the email. If you do not set this value, the address: donotreply@smartsimple.com will be used.
- Email To – select the internal people to receive the email.
- Subject – the subject of the email. See below for the variables that you can use in the subject.
- Body – the body of the alert email. See below for the variables that you can use in the body.
Intruder Alert Email Variables – because the user is not logged into the system, the amount of information available is limited to IP Address @ip@, the attempted username @username@ and date/time @now@ of the attempted login.
Intruder Log
The View Log tab is used to access the Intruder Alert log.
- The list can be sorted by clicking the column title.
- You can filter the list by username, year, and month.
Hierarchical Password Policy
When viewing a company in your hierarchy, select Settings > Password Policy to define.
A different password policy can be defined for each company within the system.
If there are password policies defined for a company then it will automatically apply to all sub-companies in the hierarchy, unless those sub-companies have defined their own password policy.
If there are no password policies defined for a company, then the system will look at the companies above it in the hierarchy, and if one of these parent companies have a password policy set then it will use these settings.
If there are no password policies defined for a company, or any of the companies above it in the hierarchy, then the password policy set in Global Settings will apply.
NOTE: There are no settings stored in the database for a company until someone actually opens the Password Policy page for that company and clicks Save.
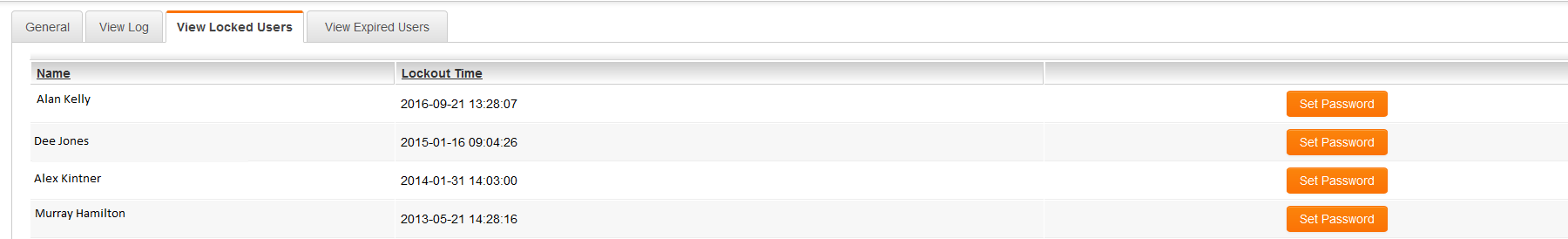
View Locked Users
This option is only available from the Password Policy on the. It cannot be accessed for the individual Password policies for the different companies in your organizations hierarchy.
The View Locked Users tab will display all users that have had their account locked.
- Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked.
- When an account has been locked for exceeding the alloted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevent would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed.
- If a user is locked, you can click on the Set Password button to reactivate the account and send the user a new password.
View Expired Users
This option is only available from the Password Policy on the. It can not be accessed for the individual Password policies for the different companies in your organizations hierarchy.
- The View Expired Users tab will display all users that had their accounts disabled due to inactivity. There will be page navigation options if there is an overly long list.
- Once an account has been expired for having been inactive for longer that the permitted number of days it will remain on the "expired users" list until their password is reset. This allows the administrator to see which users have been expired.
- If a user is expired, you can click on the Send Password button to reactivate the account and send the user a new password.
Single Sign-On
For information on the Single Sign-On settings and functionality, please refer to the Single Sign-On page.