Difference between revisions of "Security Matrix and the Shadow Applications"
Julia Decker (talk | contribs) |
|||
| (4 intermediate revisions by 3 users not shown) | |||
| Line 5: | Line 5: | ||
This matrix will control visibility through the shadow application. | This matrix will control visibility through the shadow application. | ||
| − | + | ||
| − | * | + | When accessing a [[UTA]] via a '''Shadow Application''', the Shadow [[Application]] will: |
| − | + | * Use the parent '''Security Matrix''' if the Security Matrix has not been enabled in the Shadow Application | |
| + | ::and | ||
| + | * Use the parent '''Application Scope Access''' if Application Scope Access has not been enabled in the Shadow Application. | ||
| + | |||
| + | If the '''Security Matrix''' or '''Application Scope Access''' have been enabled in the Shadow UTA they will override those of the parent UTA. | ||
==Enabling a Shadow Application Security Matrix== | ==Enabling a Shadow Application Security Matrix== | ||
| Line 27: | Line 31: | ||
Next you will create a matrix within this application. | Next you will create a matrix within this application. | ||
| − | 5. Click '''Settings''', | + | 5. Click '''Settings''', and then on the [[UTA Settings - Security|Security tab]]. |
6. Click the '''Enable Security Matrix''' check box. | 6. Click the '''Enable Security Matrix''' check box. | ||
| Line 55: | Line 59: | ||
As you have not set any list view there is no way to drill down to an individual contract. | As you have not set any list view there is no way to drill down to an individual contract. | ||
| − | [[ | + | ==Setting the List View in a Shadow Application== |
| + | |||
| + | Setting the list view is exactly the same for all Universal Tracking [[Application|applications]]. | ||
| + | |||
| + | 1. Click the '''Settings''' tab. | ||
| + | |||
| + | 2. Click the '''List View''' link. | ||
| + | |||
| + | Only the fields selected in this application are displayed. | ||
| + | |||
| + | [[Image:Uta400.png]] | ||
| + | |||
| + | 3. Set the fields as shown below: | ||
| + | |||
| + | [[Image:Uta399.png]] | ||
| + | |||
| + | 4. Click the '''Save''' button. | ||
| + | |||
| + | 5. Click the '''Contracts''' tab. | ||
| + | |||
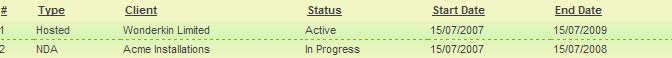
| + | The contracts are now displayed correctly. | ||
| + | |||
| + | [[Image:Uta398.png]] | ||
| + | |||
| + | Note the type and the status displayed are from the shadow application – not the parent application. | ||
| + | |||
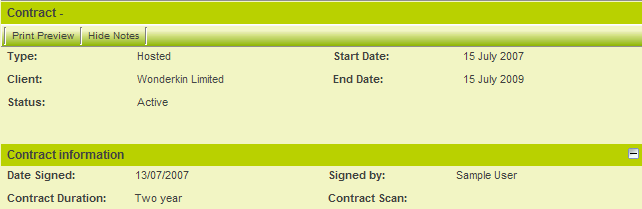
| + | 6. Click on the first contract to review the details. | ||
| + | |||
| + | [[Image:Uta397.png]] | ||
| + | |||
| + | * Only the selected standard fields are displayed. | ||
| + | * The [[Custom Field|custom fields]] are displayed. We indicated that [[Custom Field|custom fields]] should be inherited by the shadow application. | ||
| + | * The contract cannot be edited as the security matrix is providing a read-only view. | ||
| + | |||
| + | ==See Also== | ||
| + | * [[Benefits of a Shadow Application]] | ||
| + | * [[Creating and Enabling a Shadow Application]] | ||
| + | * [[Setting Manager Permission to the Shadow Application]] | ||
| + | * [[Configuring Templates and Statuses in a Shadow Application]] | ||
| + | |||
| + | {{PrevNextStart}} [[Configuring Templates and Statuses in a Shadow Application]] | ||
| + | {{PrevNextMid}} [[Integrating Email with the UTA]] | ||
| + | {{PrevNextEnd}} | ||
| + | [[Category:Universal Tracking Application]] | ||
Latest revision as of 14:39, 22 July 2013
Before you can view any data in the shadow application you need to consider the impact of the security matrix feature.
Though you have not applied the security matrix to this application, there is a security matrix in effect in the parent application.
This matrix will control visibility through the shadow application.
When accessing a UTA via a Shadow Application, the Shadow Application will:
- Use the parent Security Matrix if the Security Matrix has not been enabled in the Shadow Application
- and
- Use the parent Application Scope Access if Application Scope Access has not been enabled in the Shadow Application.
If the Security Matrix or Application Scope Access have been enabled in the Shadow UTA they will override those of the parent UTA.
Enabling a Shadow Application Security Matrix
In this exercise, you will activate the security matrix for the shadow application and thus override the matrix from the parent application.
1. Choose the Applications, Contracts – Customer View menu.
2. Click the Contracts tab.
3. Select both status check boxes.
4. Click the Find button.
No Items are displayed with the security matrix in place.
Next you will create a matrix within this application.
5. Click Settings, and then on the Security tab.
6. Click the Enable Security Matrix check box.
7. Click any Save button.
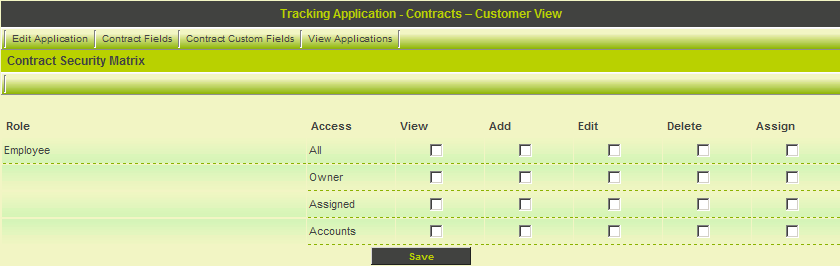
8. Click the Security Matrix link.
As you have only selected one role to access this application this is the only role available.
The matrix is only available for Level 1 items as you did not include Level 2 or 3 in the shadow application.
9. Set the View Permission for All.
10. Click the Save button.
11. Click Contracts tab.
The contracts are displayed.
As you have not set any list view there is no way to drill down to an individual contract.
Setting the List View in a Shadow Application
Setting the list view is exactly the same for all Universal Tracking applications.
1. Click the Settings tab.
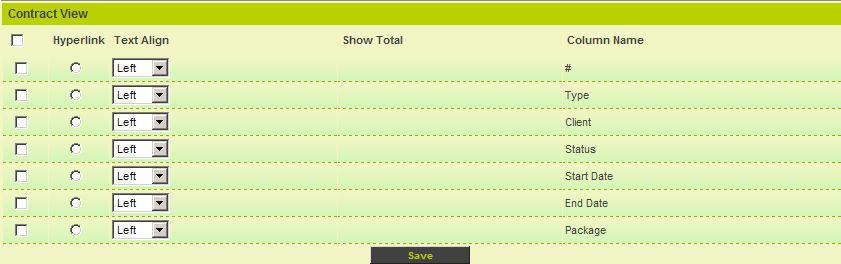
2. Click the List View link.
Only the fields selected in this application are displayed.
3. Set the fields as shown below:
4. Click the Save button.
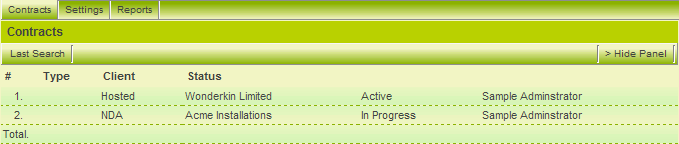
5. Click the Contracts tab.
The contracts are now displayed correctly.
Note the type and the status displayed are from the shadow application – not the parent application.
6. Click on the first contract to review the details.
- Only the selected standard fields are displayed.
- The custom fields are displayed. We indicated that custom fields should be inherited by the shadow application.
- The contract cannot be edited as the security matrix is providing a read-only view.
See Also
- Benefits of a Shadow Application
- Creating and Enabling a Shadow Application
- Setting Manager Permission to the Shadow Application
- Configuring Templates and Statuses in a Shadow Application