Difference between revisions of "System Security Summary"
Greg Stanley (talk | contribs) |
|||
| (27 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
| − | |||
__TOC__ | __TOC__ | ||
=Overview= | =Overview= | ||
| − | + | The '''System Security Summary '''allows you to review the acccess risk of your current [[instance]] configuration. It can be found on the '''Global Settings '''area of your system. It will run an assessment of the security items in your system each time you click into the '''System Security Summary '''hyperlink, providing you with real-time evaluation of your system security. | |
| + | |||
| + | '''Note: '''You will need to have [[Global User Administrator|System Administrator]] access to both view and run the '''System Security Summary. ''' | ||
| − | =Accessing the System Security Summary= | + | =Configuration - Essentials= |
| + | ===Accessing the System Security Summary=== | ||
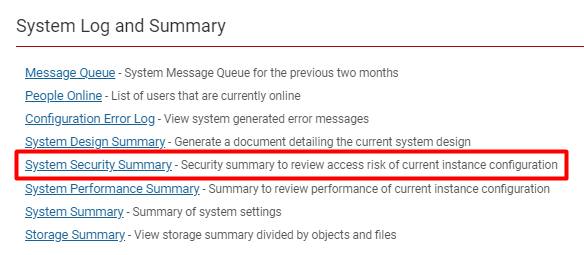
To access the '''System Security Summary''', follow these steps: | To access the '''System Security Summary''', follow these steps: | ||
| Line 19: | Line 20: | ||
:: [[File:System security summary.png|thumb|none|500px|The System Security Summary hyperlink found under System Log and Summary]] | :: [[File:System security summary.png|thumb|none|500px|The System Security Summary hyperlink found under System Log and Summary]] | ||
| − | =System Security Summary | + | ===Using the System Security Summary=== |
| + | The benefit of the '''System Security Summary '''is that you can see in one, organized place where all of your system security measures are, and what is lacking in each of them. | ||
| + | |||
| + | In order to improve your system security. simply click the '''URL '''button on the left side of the security item in the '''System Security Summary. ''' | ||
| + | |||
| + | * '''Note: '''You only need to fix the items that have a '''Attention Required '''icon under the '''Attention Required '''column. | ||
| + | |||
| + | :: [[File:Fixing sys security summary.png|thumb|none|900px|Important details about an Attention Required security setting.]] | ||
| + | This section will bring you through a step-by-step example of fixing the security vulnerability of the '''Password Policy '''which has been indicated on the '''System Security Summary.''' | ||
| + | |||
| + | 1. First, [[System Security Summary#Accessing the System Security Summary|go to the System Security Summary]]. | ||
| + | |||
| + | 2. Find the security item you would like to configure the security settings for from the [[List View Overview|list]]. The item should have a '''red caution '''icon under the '''Attention Required '''column so that you know the security measures need to be changed. You can also look at the level of severity under the '''Severity '''column to gauge how critical the security vulnerability is. | ||
| + | |||
| + | * In this example, the feature is '''Password Policy. ''' | ||
| + | |||
| + | 3. Read the text inputted into the '''Details '''column, as this will explain what the security vulnerability for the feature is. | ||
| + | |||
| + | * In this case, the issue is that "Password Expiration must be greater than 0." | ||
| + | |||
| + | 4. Click on the '''arrow icon '''under the '''URL '''column. This will bring you directly to the configuration page of where that security feature is found. | ||
| + | |||
| + | * In this case, the '''URL '''function brings us to the [[Password Policy|Password and Activation Policies]] part of the system. | ||
| + | |||
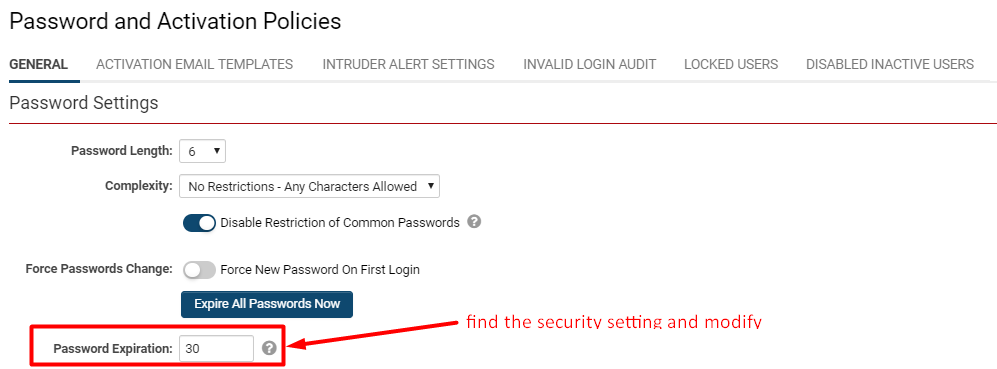
| + | 5. Locate the specific setting(s) mentioned in the '''Details '''column and modify that setting to increase the security. | ||
| + | |||
| + | :: [[File:System security summary fix.png|thumb|none|700px|Once in the settings of the security feature, locate the specific issue and modify that setting so that the security is no longer vulnerable.]] | ||
| + | 6. Click '''Save. ''' | ||
| + | |||
| + | 7, Returning to the '''System Security Summary, '''that specific security feature should be now marked as '''Safe ('''[[File:Sys security summary approved icon 2019.png]]) under th'''e Attention Required '''column. | ||
| + | |||
| + | =System Security Summary - Settings Explained= | ||
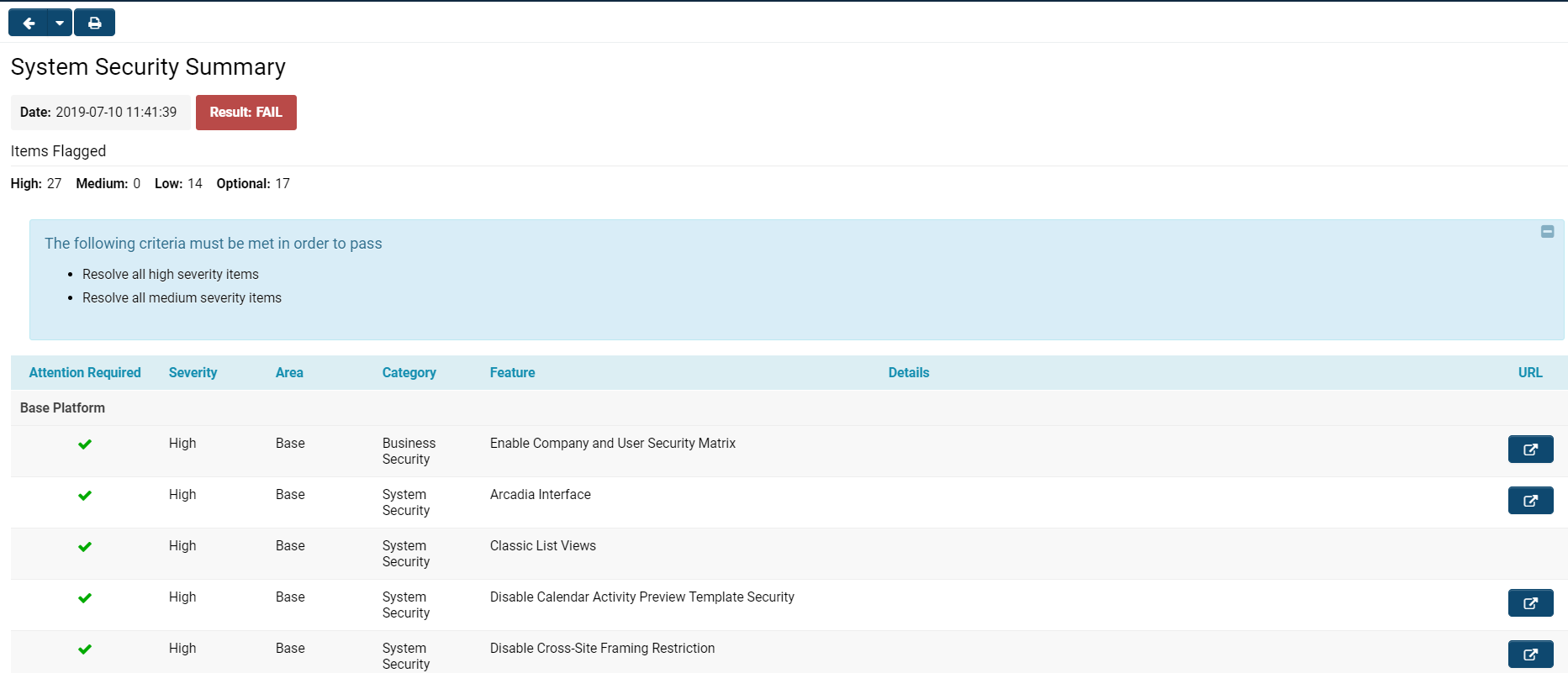
When you open the '''System Security Summary''', you will see a page displayed with details similar to those in the image below: | When you open the '''System Security Summary''', you will see a page displayed with details similar to those in the image below: | ||
| Line 25: | Line 57: | ||
The '''System Security Summary '''has different components. | The '''System Security Summary '''has different components. | ||
| + | At the very top left of your page are two buttons: | ||
| + | |||
| + | :: [[File:Sys security summary buttons.png|border]] | ||
| + | : | ||
| + | :* The '''right arrow '''allows you to go back to the last page that you were from (typically the [[Global Settings]] page from which you accessed the '''System Security Summary.''' | ||
| + | :* Clicking the '''drop down arrow '''will allow you to choose from a list of several of the most recent pages you accessed. | ||
| + | :* The '''printer icon '''will allow you to print a PDF report of all the system security summary information in the same list and structure as is organized on the page in the platform. | ||
| + | Below these buttons and right underneath the '''System Security Summary '''title, you will see the following information: | ||
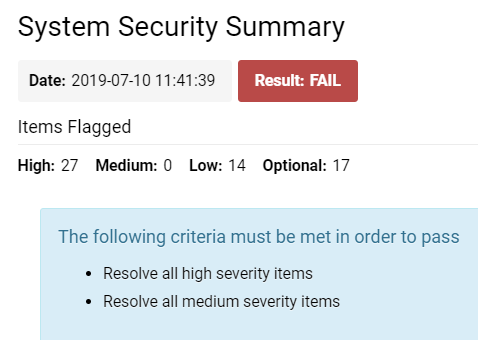
:: [[File:Sys security summary top 20219.png|thumb|none|300px|The System Security Summary settings displayed at the top of your page.]] | :: [[File:Sys security summary top 20219.png|thumb|none|300px|The System Security Summary settings displayed at the top of your page.]] | ||
| − | + | {| class="wikitable" | |
| + | |- | ||
| + | ||'''Date''' | ||
| + | ||The time and date stamp of when the system security summary was most recently run - this will be the time that you clicked into the '''System Security Summary '''hyperlink from [[Global Settings]]. | ||
| + | |- | ||
| + | ||'''Result''' | ||
| + | ||This will be the result generated from your most recent run of the system security. It will either be a '''FAIL '''(red) or '''PASS '''(green). | ||
| + | |- | ||
| + | ||'''Items Flagged''' | ||
| + | || | ||
| + | '''High - '''The number of items in the system that the system security counts as high severity. It is highly recommended to change the security settings on high severity items; otherwise, your system security is vulnerable and insecure. | ||
| + | |||
| + | '''Medium - '''The number of items in the system that the system security counts as medium severity. It is recommended to change the security settings on medium severity items to improve your overall system security. | ||
| + | |||
| + | '''Low - '''The number of items in the system that the system security summary counts as low severity; you are recommended to change the security settings on these low severity items, but it will not be a critical detriment to your overall system security. | ||
| + | |||
| + | '''Optional - '''These are the number of items in the system that the system security does not mandate you need to improve the security on. You can choose whether or not you want to increase the security settings on these items. | ||
| + | |||
| + | |- | ||
| + | ||'''The following criteria must be met in order to pass''' | ||
| + | ||This text box that appears at the top of your '''System Security Summary '''page will give you a list of the steps necessary in order to change your security status from '''FAIL '''to '''PASS. '''In this example, for instance, a [[Global User Administrator|System Administrator]] should resolve all high severity items and all medium severity items. Once they do so, running their''' System Security Summary''' again should ensure that they get a '''PASS '''status. | ||
| + | |} | ||
| + | Below these top notifications is the [[List View Overview|list view]] of System Security features. | ||
| + | |||
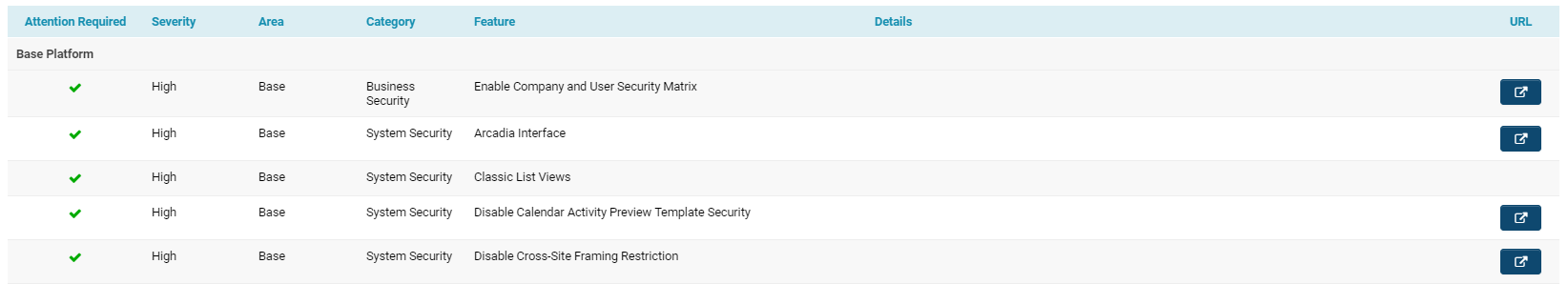
| + | ::: [[File:Sys security summary list view.png|thumb|none|1000px|List view of System Security features.]] | ||
| + | The columns included in the list view for System Security are each explained below: | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| + | !|Column | ||
| + | !|Function | ||
| + | |- | ||
| + | ||'''Attention Required''' | ||
|| | || | ||
| − | || | + | [[File:Sys security summary attention required icon 2019.png]] - '''Attention Required: '''If attention is required on a system item, there will be a warning icon. |
| + | |||
| + | [[File:Sys security summary approved icon 2019.png]] - '''Safe: '''If no attention is required on a system item, there will be a green check mark icon. | ||
| + | |||
| + | |- | ||
| + | ||'''Severity''' | ||
| + | ||'''High, Medium '''and '''Low '''severity level will be listed for all security items, corresponding to the level of severity for each item. | ||
|- | |- | ||
| + | ||'''Area''' | ||
|| | || | ||
| − | || | + | '''Base - '''A security item with a '''Base '''area indicates that the feature exists in the '''Base Platform. '''These are security settings that impact the user experience of the overall system, such as the [[:Category:Arcadia|Arcadia]] interface, [[Login Page|login accessibility]], [[APIs]] and more. |
| + | |||
| + | '''[[Universal Tracking Application|UTA]] - '''A security item with a '''UTA '''area indicates that the feature exists specifically to an application in the system. Any '''UTA '''security item will be listed under a heading that specifically names which UTA it is relevant to. '''UTA '''security items can be associated with {{L1}}, {{L2}}, or {{L3}} settings. | ||
| + | |||
|- | |- | ||
| + | ||'''Category''' | ||
|| | || | ||
| − | || | + | Every security item will fall under a broad category. |
| + | |||
| + | '''[[Security Settings#Business Security Settings|Business Security]] - '''Any security item that can be found in the '''Global Settings > Security > Business Security '''setting. | ||
| + | |||
| + | '''[[Security Settings#System Security Settings|System Security]] - '''Any security item that can be found in the '''Global Settings > Security > System Security '''setting. | ||
| + | |||
| + | '''[[Usability]] - '''Any security item that is concerned with the usability of the platform; in other words, if this security item will impact the user's experience and interaction with the [[SmartSimple]] [[:Category:Interface|interface]]. | ||
| + | |||
| + | '''Security - '''Any security item that falls under the [[Security Matrix]] for {{L1}}, {{L2}} or {{L3}} [[Entity|entities]] in a [[Universal Tracking Application|UTA]]. | ||
| + | |||
|- | |- | ||
| − | || | + | ||'''Feature''' |
| − | || | + | ||The name of the security feature. Some examples might include [[List Views Overview|Classic List Views]], [[:Category:Arcadia|Arcadia Interface]], [[Login Page#Disable Login Token Check|Disable Login Token Check]], [[APIs|Enable Desktop API]], [[Reports]], [[Password Policy]], [[Configuring a SmartSimple Instance#Enable SSL (secure Socket Layer)|Enable SSL]], and more. |
|- | |- | ||
| + | ||'''Details''' | ||
|| | || | ||
| − | | | + | This will provide more information about what the security risk is. |
| + | |||
| + | For example, for the [[Password Policy]] feature, a '''High Severity, Attention Required '''issue might have the details '''Password Expiration must be greater than 0. ''' | ||
| + | |||
| + | In other cases, the '''Details '''column for a security item might simply include a list of data relevant to the feature; for example, '''SmartSimple User Accounts '''will include a list of all [[User|user]]'s emails who are in that [[instance]]. | ||
| + | |||
|- | |- | ||
| + | ||'''URL''' | ||
|| | || | ||
| − | + | [[File:URL button sys security.png]] - '''Go to Settings: '''The '''outward arrow '''icon will appear under the '''URL '''column for each feature item. | |
| + | |||
| + | Clicking on the button that corresponds to the item will bring you to the part of the system that allows you to configure the security settings. For example, clicking on this button for a '''High Severity, Attention Required, UTA''' security row might bring you to the security matrix for that {{UTA}}'s {{L1}} [[entity]]. You can then permission the security settings on that page appropriately based on the '''Details '''provided with the security risk. | ||
| + | |||
|} | |} | ||
| + | |||
| + | =See Also= | ||
| + | * [[Security Settings]] | ||
| + | * [[Security Matrix]] | ||
| + | * [[Role Based Security]] | ||
| + | |||
| + | [[Category:System Management]][[Category:Security]] | ||
Latest revision as of 21:38, 15 February 2022
Contents
Overview
The System Security Summary allows you to review the acccess risk of your current instance configuration. It can be found on the Global Settings area of your system. It will run an assessment of the security items in your system each time you click into the System Security Summary hyperlink, providing you with real-time evaluation of your system security.
Note: You will need to have System Administrator access to both view and run the System Security Summary.
Configuration - Essentials
Accessing the System Security Summary
To access the System Security Summary, follow these steps:
1. Click on the 9-square menu icon on the top right of your page.
2. Under the heading Configuration, select Global Settings.
3. Under the first tab (labelled System) scroll down to the bottom of the page to the subsection labelled System Log and Summary.
4. Click on the hyperlink labelled System Security Summary.
Using the System Security Summary
The benefit of the System Security Summary is that you can see in one, organized place where all of your system security measures are, and what is lacking in each of them.
In order to improve your system security. simply click the URL button on the left side of the security item in the System Security Summary.
- Note: You only need to fix the items that have a Attention Required icon under the Attention Required column.
This section will bring you through a step-by-step example of fixing the security vulnerability of the Password Policy which has been indicated on the System Security Summary.
1. First, go to the System Security Summary.
2. Find the security item you would like to configure the security settings for from the list. The item should have a red caution icon under the Attention Required column so that you know the security measures need to be changed. You can also look at the level of severity under the Severity column to gauge how critical the security vulnerability is.
- In this example, the feature is Password Policy.
3. Read the text inputted into the Details column, as this will explain what the security vulnerability for the feature is.
- In this case, the issue is that "Password Expiration must be greater than 0."
4. Click on the arrow icon under the URL column. This will bring you directly to the configuration page of where that security feature is found.
- In this case, the URL function brings us to the Password and Activation Policies part of the system.
5. Locate the specific setting(s) mentioned in the Details column and modify that setting to increase the security.
6. Click Save.
7, Returning to the System Security Summary, that specific security feature should be now marked as Safe (![]() ) under the Attention Required column.
) under the Attention Required column.
System Security Summary - Settings Explained
When you open the System Security Summary, you will see a page displayed with details similar to those in the image below:
The System Security Summary has different components.
At the very top left of your page are two buttons:
-
- The right arrow allows you to go back to the last page that you were from (typically the Global Settings page from which you accessed the System Security Summary.
- Clicking the drop down arrow will allow you to choose from a list of several of the most recent pages you accessed.
- The printer icon will allow you to print a PDF report of all the system security summary information in the same list and structure as is organized on the page in the platform.
Below these buttons and right underneath the System Security Summary title, you will see the following information:
| Date | The time and date stamp of when the system security summary was most recently run - this will be the time that you clicked into the System Security Summary hyperlink from Global Settings. |
| Result | This will be the result generated from your most recent run of the system security. It will either be a FAIL (red) or PASS (green). |
| Items Flagged |
High - The number of items in the system that the system security counts as high severity. It is highly recommended to change the security settings on high severity items; otherwise, your system security is vulnerable and insecure. Medium - The number of items in the system that the system security counts as medium severity. It is recommended to change the security settings on medium severity items to improve your overall system security. Low - The number of items in the system that the system security summary counts as low severity; you are recommended to change the security settings on these low severity items, but it will not be a critical detriment to your overall system security. Optional - These are the number of items in the system that the system security does not mandate you need to improve the security on. You can choose whether or not you want to increase the security settings on these items. |
| The following criteria must be met in order to pass | This text box that appears at the top of your System Security Summary page will give you a list of the steps necessary in order to change your security status from FAIL to PASS. In this example, for instance, a System Administrator should resolve all high severity items and all medium severity items. Once they do so, running their System Security Summary again should ensure that they get a PASS status. |
Below these top notifications is the list view of System Security features.
The columns included in the list view for System Security are each explained below:
| Column | Function |
|---|---|
| Attention Required |
|
| Severity | High, Medium and Low severity level will be listed for all security items, corresponding to the level of severity for each item. |
| Area |
Base - A security item with a Base area indicates that the feature exists in the Base Platform. These are security settings that impact the user experience of the overall system, such as the Arcadia interface, login accessibility, APIs and more. UTA - A security item with a UTA area indicates that the feature exists specifically to an application in the system. Any UTA security item will be listed under a heading that specifically names which UTA it is relevant to. UTA security items can be associated with Level 1, Level 2, or Level 3 settings. |
| Category |
Every security item will fall under a broad category. Business Security - Any security item that can be found in the Global Settings > Security > Business Security setting. System Security - Any security item that can be found in the Global Settings > Security > System Security setting. Usability - Any security item that is concerned with the usability of the platform; in other words, if this security item will impact the user's experience and interaction with the SmartSimple interface. Security - Any security item that falls under the Security Matrix for Level 1, Level 2 or Level 3 entities in a UTA. |
| Feature | The name of the security feature. Some examples might include Classic List Views, Arcadia Interface, Disable Login Token Check, Enable Desktop API, Reports, Password Policy, Enable SSL, and more. |
| Details |
This will provide more information about what the security risk is. For example, for the Password Policy feature, a High Severity, Attention Required issue might have the details Password Expiration must be greater than 0. In other cases, the Details column for a security item might simply include a list of data relevant to the feature; for example, SmartSimple User Accounts will include a list of all user's emails who are in that instance. |
| URL |
Clicking on the button that corresponds to the item will bring you to the part of the system that allows you to configure the security settings. For example, clicking on this button for a High Severity, Attention Required, UTA security row might bring you to the security matrix for that 's Level 1 entity. You can then permission the security settings on that page appropriately based on the Details provided with the security risk. |