Difference between revisions of "UTA Security Matrix"
(→Setting Role-Based Security Permissions) |
|||
| (28 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | == | + | ==Overview== |
| + | The '''UTA Security Matrix '''feature in your [[SmartSimple]] [[instance]] allows you to restrict [[User|user]]'s interaction with the [[Universal Tracking Application|Universal Tracking Applications]] in your system and the associated [[entities]] with each application. The '''Security Matrix '''allows you to define how users can interact with each level of the data in an application, based on the way that they need to interact with data. You must enable the '''Security Matrix '''and permission each [[User Role|role]] to have varying levels of accessibility to the [[Universal Tracking Application]]. | ||
| − | + | '''Note: '''You must have [[Global User Administrator|System Administrator]] privileges in order to enable the '''Security Matrix.''' | |
| − | + | ==Configuration - Essentials== | |
| + | ===Enabling the Security Matrix=== | ||
| + | Your first step is to create the [[Universal Tracking Application|Universal Tracking Applications]] for your system. If and once these have already been created, you may then enable the '''Security Matrix '''feature to ensure that the levels of access dependent on [[User Role|user role]] are properly secure and permissioned. | ||
| − | + | 1. Open the {{UTA}} whose security you would like to permission. | |
| − | + | 2. Click the '''gear icon '''on the top left of the UTA page in order to enter its '''Configuration Settings.''' | |
| − | + | :: [[File:UTA configuration.png]] | |
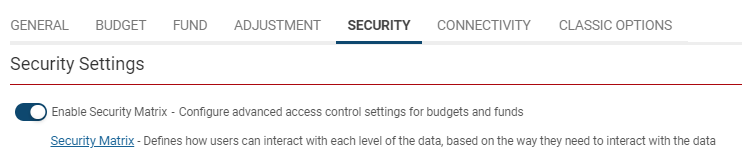
| + | 3. Click into the '''Security '''tab. | ||
| − | + | 4. Toggle on the '''Enable Security Matrix '''option. | |
| − | + | 5. A '''Security Matrix '''hyperlink will then appear below. Click this hyperlink. | |
| − | |||
| − | |||
| − | + | :: [[File:UTA security matrix.png|500px|border]] | |
| + | <pre>As soon as the Security Matrix is enabled, all users will lose all access to data within the application until the role-specific permissions are established. </pre> | ||
| − | The '''Security Matrix''' | + | ===Setting Role-Based Security Permissions=== |
| + | The next step after clicking into the '''Security Matrix''' hyperlink is to specifically choose which roles will have which security permissions with this {{UTA}}. | ||
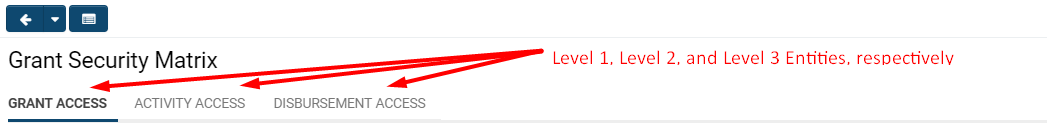
| − | + | The {{UTA}} '''Security Matrix''' page will appear with a top row of tabs that lead, chronologically, to the security matrices of the {{L1}}, {{L2}}, and {{L3}} entities in that UTA (if more than a {{L1}} entity is applicable). | |
| − | |||
| − | |||
| − | + | :: [[File:Security matrix grant manager 2019.png|thumb|none|800px|Grant Manager Security Matrix example, with tabs for L2, L2, and L3 entities]] | |
| + | In each security matrix is a list of the respective UTA [[User Role|user roles]], followed by these column headings: '''Access''', '''Deny''', '''View''', '''Add''', '''Edit''', '''Delete''', and '''Assign.''' | ||
| + | :: [[File:Security matrix budget manager column headings.png|thumb|none|1200px|Security Matrix column headings in list view.]] | ||
| + | Choose the [[roles]] that should have access to the application in the [[UTA_Settings_-_Security#Access_Role_Settings|Access Role Settings]] box. Only the roles added to [[UTA_Settings_-_Security#Access_Role_Settings|Access Role Settings]] are made available to be configured in the Security Matrix. | ||
| + | Click the ''Save'' button again. | ||
| + | Click the '''Security Matrix''' link. | ||
The Security Matrix window is displayed. | The Security Matrix window is displayed. | ||
| + | [[File:Security Matrix Example.png|800px|border]] | ||
| − | |||
| − | |||
==How the Security Matrix works== | ==How the Security Matrix works== | ||
| + | * The current view is for security associated with the Grant level ({{l1}}). | ||
| − | * | + | * '''Two additional tabs''' are used to control security associated with the Activity ({{l2}}) and Level 3 Activity levels. |
| − | + | For each [[Role|role]] that you have permissioned to access the application in the "[[UTA_Settings_-_Security#Access_Role_Settings|Access Role Settings]]," the same set of options will be displayed at each level. | |
| − | |||
| − | For each [[Role|role]] that you have permissioned to access the [[ | ||
==Role Engagement== | ==Role Engagement== | ||
| + | All access is [[Role|role]] based. Each set of access permissions can be set based on the following role engagement: | ||
| − | |||
* '''All''' – All [[User|users]] in this [[Role|role]] can perform the permissioned actions. | * '''All''' – All [[User|users]] in this [[Role|role]] can perform the permissioned actions. | ||
| − | * '''Owner''' – Only a [[User|user]] in this [[Role|role]] associated through the | + | * '''Owner''' – Only a [[User|user]] in this [[Role|role]] associated through the "Owner" standard field can perform the permissioned actions. |
| − | * '''Assigned''' – Only [[User|users | + | * '''Assigned''' – Only [[User|users]] that are assigned to the item - either in the "Assigned" standard field or assigned as a contact with this role - can perform the permissioned actions. |
| − | * ''' | + | * '''Organizations''' – Only [[User|users]] in this [[Role|role]] that are associated with organizations assigned to this item can perform the permissioned actions. This is an indirect permission. For example, if you were to associate a company with a project and use this permission, then someone from that company with this [[Role|role]] would be able to perform the permissioned actions. |
| + | * '''Person''' - Only [[User|users]] in this [[Role|role]] associated through the "Person" standard field can perform the permissioned actions. | ||
==Permission Types== | ==Permission Types== | ||
| + | The following six permission types are available: | ||
| − | + | * '''Deny''' - Users in this role are denied access to this item. | |
* '''View''' – View the item. | * '''View''' – View the item. | ||
* '''Add''' – Create a new item. | * '''Add''' – Create a new item. | ||
| Line 57: | Line 64: | ||
==Setting the Security Matrix== | ==Setting the Security Matrix== | ||
| + | 1. Set the '''permissions''' as shown below: | ||
| − | + | [[Image:SecurityMatrixExample.png|link=]] | |
| − | + | * All Employees can view all items. | |
| − | + | * Only the Employee assigned as the "Owner" of a given record can view, add, edit, delete and assign other people to that record. | |
| − | * All | ||
| − | * Only the | ||
2. Click the '''Save''' button. | 2. Click the '''Save''' button. | ||
| Line 69: | Line 75: | ||
3. Click the '''Activity Access''' tab. | 3. Click the '''Activity Access''' tab. | ||
| − | The same set of [[Role|roles]] and permissions are displayed, but this time for the | + | The same set of [[Role|roles]] and permissions are displayed, but this time for the {{l2}} items. |
| + | |||
| + | [[Image:SecurityMatrixL2.png|link=]] | ||
| − | |||
| − | |||
4. Set the permissions the same as for the Level 1 items. | 4. Set the permissions the same as for the Level 1 items. | ||
5. Click the '''Save''' button. | 5. Click the '''Save''' button. | ||
| − | 6. Repeat this process for '''Level 3 | + | 6. Repeat this process for '''Level 3 Activities'''. |
| − | |||
| − | |||
| + | {{PrevNextStart}} [[Calculating Information between Levels]] | ||
| + | {{PrevNextMid}} [[Reader Logs]] {{PrevNextEnd}} | ||
[[Category:Universal Tracking Application]][[Category:Security]] | [[Category:Universal Tracking Application]][[Category:Security]] | ||
Latest revision as of 10:23, 14 December 2022
Contents
Overview
The UTA Security Matrix feature in your SmartSimple instance allows you to restrict user's interaction with the Universal Tracking Applications in your system and the associated entities with each application. The Security Matrix allows you to define how users can interact with each level of the data in an application, based on the way that they need to interact with data. You must enable the Security Matrix and permission each role to have varying levels of accessibility to the Universal Tracking Application.
Note: You must have System Administrator privileges in order to enable the Security Matrix.
Configuration - Essentials
Enabling the Security Matrix
Your first step is to create the Universal Tracking Applications for your system. If and once these have already been created, you may then enable the Security Matrix feature to ensure that the levels of access dependent on user role are properly secure and permissioned.
1. Open the whose security you would like to permission.
2. Click the gear icon on the top left of the UTA page in order to enter its Configuration Settings.
3. Click into the Security tab.
4. Toggle on the Enable Security Matrix option.
5. A Security Matrix hyperlink will then appear below. Click this hyperlink.
As soon as the Security Matrix is enabled, all users will lose all access to data within the application until the role-specific permissions are established.
Setting Role-Based Security Permissions
The next step after clicking into the Security Matrix hyperlink is to specifically choose which roles will have which security permissions with this .
The Security Matrix page will appear with a top row of tabs that lead, chronologically, to the security matrices of the Level 1, Level 2, and Level 3 entities in that UTA (if more than a Level 1 entity is applicable).
In each security matrix is a list of the respective UTA user roles, followed by these column headings: Access, Deny, View, Add, Edit, Delete, and Assign.
Choose the roles that should have access to the application in the Access Role Settings box. Only the roles added to Access Role Settings are made available to be configured in the Security Matrix.
Click the Save button again.
Click the Security Matrix link.
The Security Matrix window is displayed.
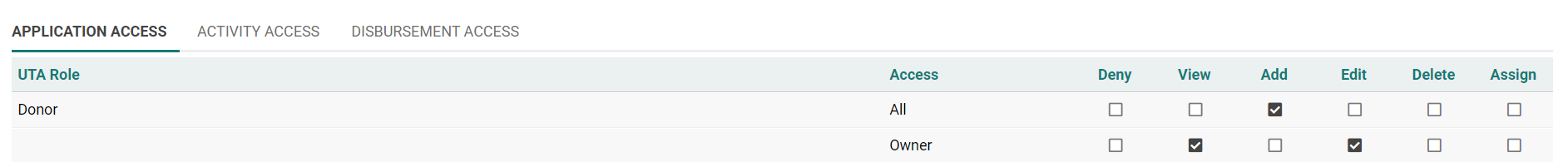
How the Security Matrix works
- The current view is for security associated with the Grant level (Level 1).
- Two additional tabs are used to control security associated with the Activity (Level 2) and Level 3 Activity levels.
For each role that you have permissioned to access the application in the "Access Role Settings," the same set of options will be displayed at each level.
Role Engagement
All access is role based. Each set of access permissions can be set based on the following role engagement:
- All – All users in this role can perform the permissioned actions.
- Owner – Only a user in this role associated through the "Owner" standard field can perform the permissioned actions.
- Assigned – Only users that are assigned to the item - either in the "Assigned" standard field or assigned as a contact with this role - can perform the permissioned actions.
- Organizations – Only users in this role that are associated with organizations assigned to this item can perform the permissioned actions. This is an indirect permission. For example, if you were to associate a company with a project and use this permission, then someone from that company with this role would be able to perform the permissioned actions.
- Person - Only users in this role associated through the "Person" standard field can perform the permissioned actions.
Permission Types
The following six permission types are available:
- Deny - Users in this role are denied access to this item.
- View – View the item.
- Add – Create a new item.
- Edit – Edit an existing item.
- Delete – Delete an existing item.
- Assign – Assign other contacts to the item.
Setting the Security Matrix
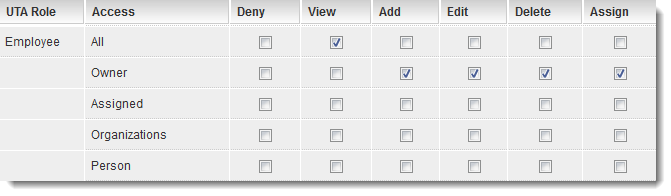
1. Set the permissions as shown below:
- All Employees can view all items.
- Only the Employee assigned as the "Owner" of a given record can view, add, edit, delete and assign other people to that record.
2. Click the Save button.
3. Click the Activity Access tab.
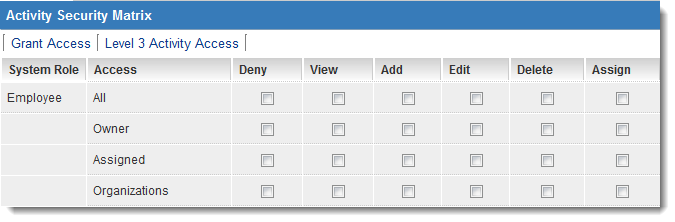
The same set of roles and permissions are displayed, but this time for the Level 2 items.
4. Set the permissions the same as for the Level 1 items.
5. Click the Save button.
6. Repeat this process for Level 3 Activities.