Difference between revisions of "Multi-Factor Authentication"
| Line 1: | Line 1: | ||
__TOC__ | __TOC__ | ||
| − | + | =Overview= | |
| − | + | When using '''Two-Factor Authentication, '''each new user can use the Google Authenticator app to obtain one-time passwords which are calculated from time and/or event-based algorithms. | |
| − | |||
| − | + | Most websites that a user can log into require a username and password, both "known" by the individual in order to log in. In short, this means that anyone who knows the correct username and password combination for a unique account can log into that account; thus, there is very little that can be done to identify that the individual logging is is actually the individual who owns the account. | |
| + | |||
| + | The '''Two-Factor Authentication '''function provides a second factor - this can be something that someone has (for example, an access card) or some unique property of that person (for example, a fingerprint, or a code sent to a personal mobile device). | ||
| + | |||
| + | A user may lose an access card or get duped into sharing a password, but the odds of both happening are dramatically reduced. Using '''Two-Factor Authentication '''enhances an organization's ability to ensure that no one is using illegitimate means to gain access. | ||
| + | |||
| + | '''Two-Factor Authentication '''is a required component of maintaining [[SmartSimple]]'s SOC2 security status. SmartSimple supports two different '''Two-Factor Authentication '''approaches: | ||
| + | |||
| + | * '''TOTP '''([https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm Time-based One-Time Password]) - this technique uses an authentication app that is installed on a mobile phone | ||
| + | * '''RSA Disconnected Token '''- this technique requires a physical device used to generate a one-time code | ||
| + | |||
| + | <pre> This article deals specifically with the TOTP protocol. To learn more about the RSA Disconnected Token protocol, contact your account manager. </pre> | ||
| − | |||
==Configuring a Role to Use Two-Factor Authentication== | ==Configuring a Role to Use Two-Factor Authentication== | ||
Revision as of 10:07, 4 July 2019
Overview
When using Two-Factor Authentication, each new user can use the Google Authenticator app to obtain one-time passwords which are calculated from time and/or event-based algorithms.
Most websites that a user can log into require a username and password, both "known" by the individual in order to log in. In short, this means that anyone who knows the correct username and password combination for a unique account can log into that account; thus, there is very little that can be done to identify that the individual logging is is actually the individual who owns the account.
The Two-Factor Authentication function provides a second factor - this can be something that someone has (for example, an access card) or some unique property of that person (for example, a fingerprint, or a code sent to a personal mobile device).
A user may lose an access card or get duped into sharing a password, but the odds of both happening are dramatically reduced. Using Two-Factor Authentication enhances an organization's ability to ensure that no one is using illegitimate means to gain access.
Two-Factor Authentication is a required component of maintaining SmartSimple's SOC2 security status. SmartSimple supports two different Two-Factor Authentication approaches:
- TOTP (Time-based One-Time Password) - this technique uses an authentication app that is installed on a mobile phone
- RSA Disconnected Token - this technique requires a physical device used to generate a one-time code
This article deals specifically with the TOTP protocol. To learn more about the RSA Disconnected Token protocol, contact your account manager.
Configuring a Role to Use Two-Factor Authentication
- Two-Factor Authentication is configured by User Role.
- For roles that have this feature enabled, the use of Two-Factor Authentication becomes mandatory.
- Click on Roles & Permissions (located on the Configuration Menu on the left-hand navigation bar)
- Click on the hyperlink for User Roles
- Click the Edit button next to the role for which you wish to add Two-Factor Authentication
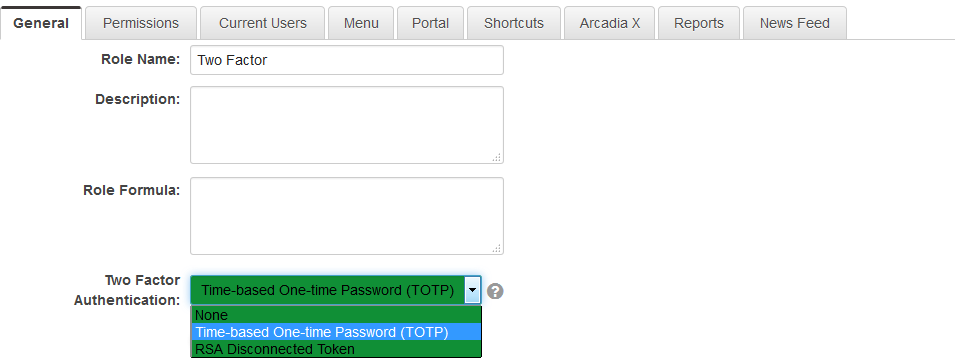
- Click on the drop-down for the Two-Factor Authentication option. There are a number of options exposed:
- None
- Time-based One-time Password (TOTP)
- RSA Disconnected Token
- Hit Save.
- Use Send Password button on user profile to send them an email with Activation link.
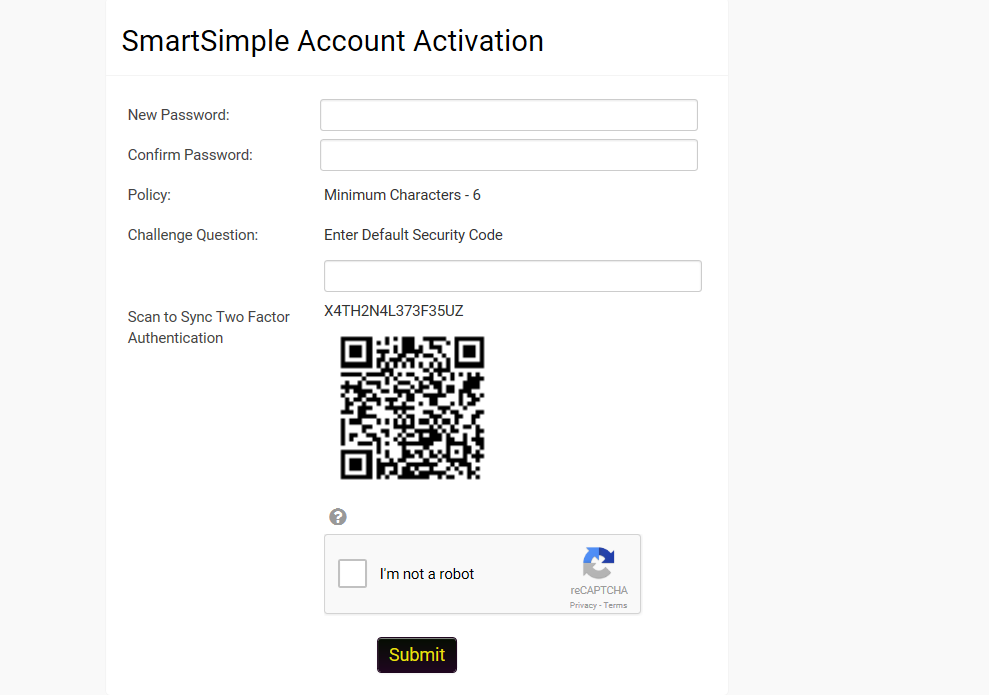
When the user receives the new password then they navigate to the activation screen.
If this is the first time the user has had a code generated then the screen should include a QR Code that can be scanned using Google Authenticator. The actual authentication code is also provided in case there are issues with the use of Google Authenticator.
If the user has an existing QA Code then the user can click a button to generate a new code and re-sync or can proceed to the login page.
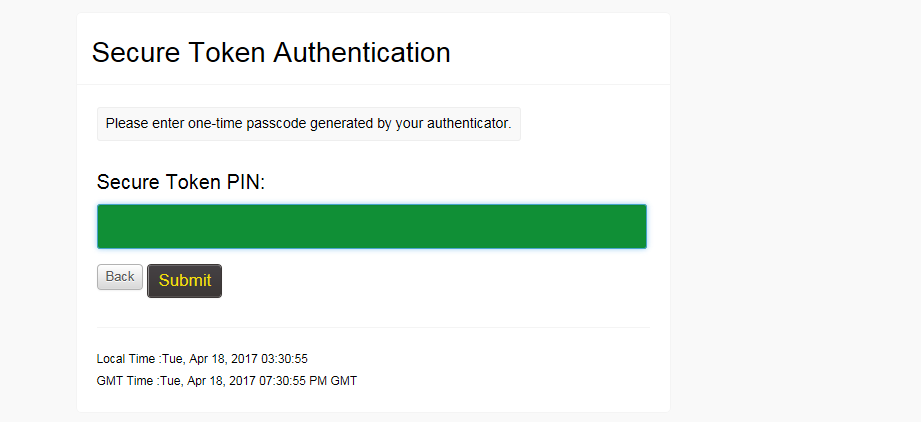
Users will then be prompted to enter the one-time code after entering their user name and password.
Notes
- If both Single Sign-On and Two-Factor Authentication are in use, there is a Single Sign-On setting option that will control whether or not Two-Factor Authentication will be required when a user authenticates via SSO.