Difference between revisions of "Password Policy"
(→Password Length and Complexity) |
(→Password Length and Complexity) |
||
| Line 3: | Line 3: | ||
==Password Length and Complexity== | ==Password Length and Complexity== | ||
| − | [[Image: | + | [[Image:PasswordPolicy.png]] |
Revision as of 14:01, 9 November 2011
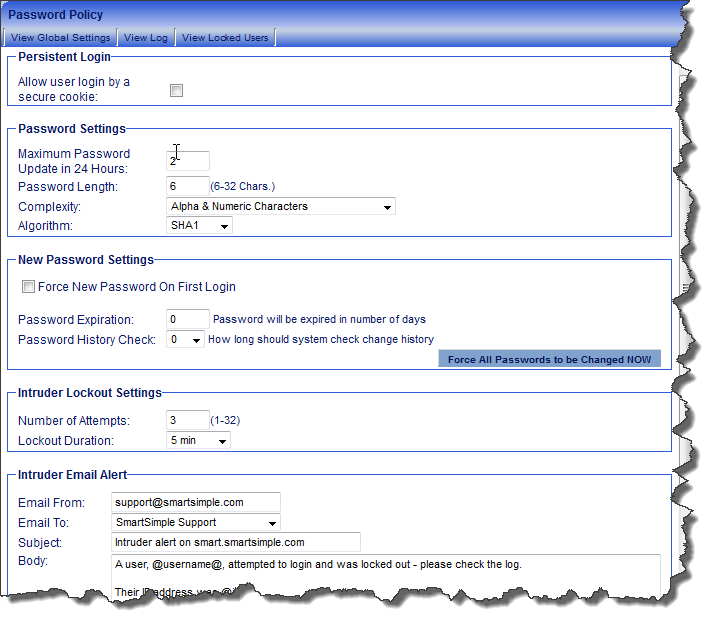
Password Policy is used to control the length and complexity of passwords, password expiration and history, the number of retries that the user is allowed, and the lockout time for the account if they exceed the number of retries.
Contents
Password Length and Complexity
Password length – the minimum length allowed for a password, between 6 and 32 characters.
Complexity – the level of complexity required in the password, the options are:
- No Restriction – any character can be used. This is the default.
- Alpha Only – only letters can be used.
- Alpha & Numeric – letters and numbers must be used in the password.
- Alpha & Numeric & Special characters – letters, numbers and special characters must be used.
- Custom Policy - a password policy can be custom defined.
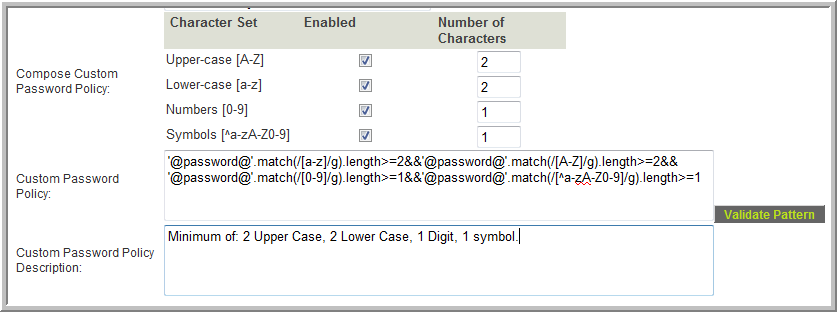
Custom Policy
- The Compose Custom Password Policy table allows you to define the custom password policy by enabling each character set desired (upper case, lower case, numeric and/or symbols) and specifying the minimum number of characters required for that character set.
- The system code used to enforce your selection will appear in the Custom Password Policy field. You can also write your own code and paste it into this field if desired.
- The Validate Pattern button will open a window where you can test various passwords against the policy to see if they will pass or fail.
- The value in the Custom Password Policy Description field will be displayed to users when setting/changing their password. You can use plain text or html in this field (For example, to insert a line break use <br>)
Important: When defining a custom password policy be sure to provide a detailed description of the policy in the Custom Password Policy Description field so that users are aware of the minimum requirement to enable them to create a valid password.
Hierarchical Password Policy
A different password policy can be defined for each company which will automatically apply to all sub-companies in the hierarchy, unless they have defined their own password policy. When viewing a company in your hierarchy, select Settings > Password Policy to define. If there are no password policies defined for a company or the companies above it in the hierarchy, the password policy set in Global Settings will apply.
New Password Settings
- Force New Password on First Login - Ensures that the user selects a password of their own choosing the first time they log into SmartSimple.
- Password Expiration - Each user will be forced to change their password once the selected number of days has passed. Any number of days can be set.
- Password History Check - You can set the number of previous passwords (to a maximum of 32) that the system will remember for each user. When changing their password, users will not be permitted to re-use a previous password until the specified number of unique passwords have been used.
Intruder Lockout Settings
These settings determine the actions that should be taken if someone attempts to log into your copy of SmartSimple.
- Number of Attempts – the number of attempts to log in with an account before the account is locked.
- Lockout Duration – the duration of the account lockout. The user will not be able to log in during this period. Period can be set to 5 minutes, 15 minutes, 30 minutes, 1 hour, 3 hours, 12 hours, 24 hours or forever (until unlocked by administrator).
- The View Locked Users tab will display all users that have had their account locked.
- If a user is locked, you can click on the Set Password button on the View Locked Users tab to reactivate the account and send the user a new password.
- Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked.
- When an account has been locked for exceeding the alloted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevent would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed.
Intruder Email Alert
These settings define who should be informed by email if an intruder alert is detected.
- Email From – the “from” address for the email. If you do not set this value, the address: support@smartsimple.com will be used.
- Email To – select the internal person to receive the email.
- Subject – the subject of the email. See below for the variables that you can use in the subject.
- Body – the body of the alert email. See below for the variables that you can use in the body.
Intruder Alert Email Variables – because the user in not logged into the system the amount of information available is limited to IP Address @ip@, the attempted username @username@ and time @time@.
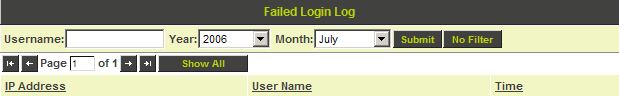
Intruder Log
The View Log tab is used to access the Intruder Alert log.
- The list can be sorted by clicking the column title.
- You can filter the list by username, year, and month.
View Locked Users
The View Locked Users tab will display all users that have had their account locked.
- Once an account has been locked for exceeding the number of permitted login attempts it will remain on the "locked users" list until the correct password is entered. This allows the administrator to see which users have been unable to log in, even if the configured lockout duration has passed and the account is no longer technically locked.
- When an account has been locked for exceeding the alloted number of attempts, after the lockout time has passed they are permitted only one attempt at the correct password. A single incorrect password at this point will re-lock the account for the configured lockout duration. In other words, once someone is on the "locked user" list they are only permitted a single wrong attempt and they will be locked for the lockout duration again. This prevent would-be intruders from having multiple attempts to guess the password each time the lockout duration has passed.