Difference between revisions of "Primary Authentication Controller"
(→Authentication Member) |
|||
| Line 52: | Line 52: | ||
|Member Alias||The [[Alias]] of the '''Authentication Member''' instance. | |Member Alias||The [[Alias]] of the '''Authentication Member''' instance. | ||
|- | |- | ||
| − | |Member URL||The [[URL]] of the '''Authentication Member''' instance (ie: '' | + | |Member URL||The [[URL]] of the '''Authentication Member''' instance (ie: ''https://alias2.smartsimple.com''). |
|- | |- | ||
|Member security key||This key provided by the '''Authentication Member''' instance. | |Member security key||This key provided by the '''Authentication Member''' instance. | ||
Revision as of 15:18, 15 May 2014
The Primary Authentication Controller feature allows one instance of SmartSimple to authenticate users to gain access to a separate instance without having to log in separately (Single Sign-On).
Note: this is only relevant to clients that use multiple instances of SmartSimple.
- The instances can reside on the same server, or on separate servers.
- This access can be granted to all users, or limited to a subset of users.
Contents
Configuration
Authentication Member
Before configuring the Primary Authentication Controller (PAC) instance you must enable Authentication Member on the target instance and generate the key that will be used by the Primary Authentication instance to gain access.
- On Global Settings within the Login & Security Settings section select the check box to enable the instance as an Authentication Member.
- Save the page and the Authentication Member Configurations link will appear.
- Within the Authentication Member Configurations page click New. Complete the details as required:
| Setting | Description |
|---|---|
| Name | Enter any name you wish. |
| Description | Enter desired description. |
| Alias | The Alias of the instance that will act as the Primary Authentication Controller. |
| Security key | This will be populated once the settings are saved. This key must be entered in the configuration of the Primary Authentication Controller instance. |
| Allow all users | Enable this setting if all login-enabled accounts within this Authentication Member instance should be allowed authenticate and connect via the Primary Authentication Controller. |
| Enabled Users | If Allow all users is not enabled this allows you to select individual user(s) that can use the Primary Authentication Controller to authenticate for this instance. |
| Create users - if not found create them automatically | Enable this setting to enable automatic creation of a new account within this instance if someone with an account on the Primary Authentication Controller attempts to connect. Note: this settings attempts to match the e-mail address to uses that are already login enabled only. If an account with the same e-mail address already exists on the Member instance, but is NOT login enabled a new user will be created when they attempt to connect. This is to avoid accidentally activating an existing contact with inappropriate pre-existing Role(s). The new user will be created with the branch and role defined in the following 2 settings. |
| Default Branch For New User | If Create users - if not found create them automatically is enabled you can select which internal branch/company they will be created within. |
| Default Role For New User | If Create users - if not found create them automatically is enabled you can select which role newly created users will be given. |
Primary Authentication Controller
To configure the instance that will act as the Primary Authentication Controller (PAC), to authenticate logins for the Authentication Member instance:
- On Global Settings within the Login & Security Settings section select the check box to enable the instance as a Primary Authentication Controller.
- Save the page and the Primary Authentication Configurations Configurations link will appear.
- Within the Primary Authentication Controller Configurations page click New. Complete the details as required:
| Setting | Description |
|---|---|
| Member Name | Enter any name you wish. |
| Description | Enter desired description. |
| Member Alias | The Alias of the Authentication Member instance. |
| Member URL | The URL of the Authentication Member instance (ie: https://alias2.smartsimple.com). |
| Member security key | This key provided by the Authentication Member instance. |
Once you have entered the above details and saved the configuration it will appear on the list of Authentication Members with a button that allows you to select which users within the Primary Authentication Controller instance are permitted to access the member instance.
Enabled Users Options
One or more of the following Enabled Users options can be set, depending on which settings are applied within the PAC and Member Authentication Controllers.
- To delete one or more configured options select the check box next to the relevant option(s) in the lower pane and click Delete.
- They cannot be edited. If a mistake is made you must delete the User Option and create it again.
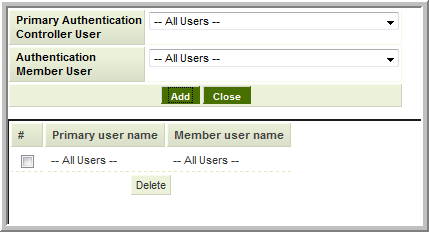
All Users to All Users
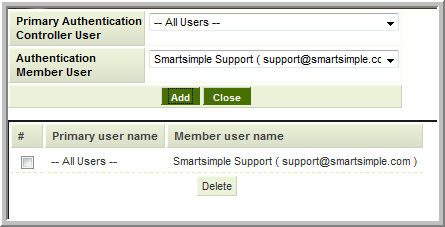
If Allow All Users is enabled on the Authentication Member instance you can set up an All Users to All Users setting. This configuration will look for an enabled user account on the Authentication Member instance that matches the e-mail address of the person logged into the PAC.
- This is the most common setting, as there is a one-to-one relationship between accounts in each instance.
- If a user on the PAC does not exist or is not enabled on the Authentication Member the user will either be denied access or a new account created, depending on the Create Users if not found setting in the Member Controller as described above.
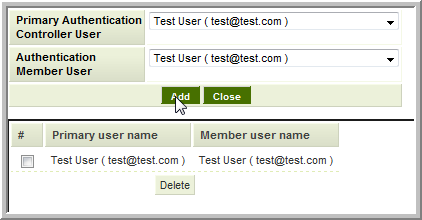
Named User to Named User
If only a select number of users on the PAC are permitted to connect to the Authentication Member instance you must define each permitted user individually.
- If All Users is enabled on the Member server you can select the individual user in the PAC User field and select the specific user in the Authentication Member User field, or set the Member User to All Users. The result will be the same as the PAC will try to match the PAC selected user's e-mail address with an enabled user with the same e-mail address on the Member Server.
- If the User isn't listed in the Member server field, but Create users if not found is enabled on the member you can select All Users as the Member user and the account will be created on the member the first time the named user on the PAC attempts to connect to the Member instance.
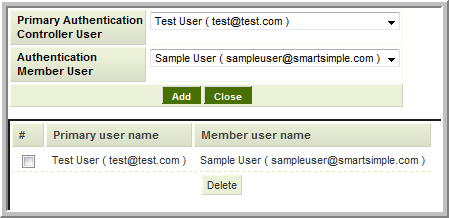
- Named User to Named User can also be used to connect accounts with different e-mail addresses on each instance
- You can configure multiple accounts on the PAC to connect to the same account on the member
- Note: each account within an instance of SmartSimple is permitted to be logged in at only one workstation. Thus if one account is connected to the member using the shared account, if/when a second person logs in to the member with the same account (whether via the PAC or by logging in directly via the Login Page) they will disconnect the first user. Accordingly caution should be used when using this configuration of sharing an account on the member server.
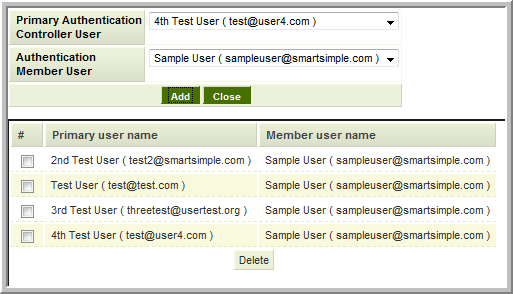
All Users to One User
Similar to configuring multiple named accounts in the PAC to connect to the same account on the member, you can enable All Users on the PAC to connect to one named account on the member.
- As above, each account within an instance of SmartSimple is permitted to be logged in at only one workstation. Thus if one account is connected to the member using the shared account, if/when a second person logs in to the member with the same account (whether via the PAC or by logging in directly via the Login Page they will disconnect the first user. Accordingly caution should be used when using this configuration of sharing an account on the member server.
Auditing
Both the Primary Authentication Controller and Authentication Member record the identity of the authenticated account on the PAC instance, the system authenticated account on the Member instance, and the date and time of connection. This can be access via reporting.
Accessing the Member Servers
- When an instance is enabled as a Primary Authentication Controller a new menu item called Authenticated Servers will appear in the Organization section of the left-side menu.
- Visibility of the Authenticated Servers menu is also controlled by the View Authenticated Servers Manager Permission.
Notes
- If the PAC for a given member instance doesn't have a Primary Authentication Controller User enabled for All Users, and your account is not specifically listed you will NOT see the server listed on the Authenticated Servers and you will NOT have access to the instance via the Authentication Controller.
- If more than one Enabled Users Options applies to a user account the All Users setting (if configured) will take precedence.
- To create a link within the PAC instance that both authenticates the user to the Authentication Member and directs them to a specific page use the following syntax:
/pacforward/memberalias/id/url_of_page_in_member_instance.jsp
Example:
/pacforward/smart/80/Apps/WFE2/wf_viewworkflows.jsp
Will connect directly to the Workflow Request page on the Member instance.
To open the link in a new tab/window append ' target='_blank
Example:
/pacforward/smart/80/Apps/WFE2/wf_viewworkflows.jsp' target='_blank