Difference between revisions of "Multi-Factor Authentication"
Ann Vincent (talk | contribs) m (→Overview) |
Ann Vincent (talk | contribs) m |
||
| Line 10: | Line 10: | ||
* '''Single Use Verification Code '''sent via email or SMS, which is better suited for external users or users who login infrequently | * '''Single Use Verification Code '''sent via email or SMS, which is better suited for external users or users who login infrequently | ||
| − | =Configuration | + | =Configuration= |
All settings related to multi-factor authentication are in a single location | All settings related to multi-factor authentication are in a single location | ||
| Line 23: | Line 23: | ||
[[File:Authentication Options.png|thumb|none|800px|Authentication Options]] | [[File:Authentication Options.png|thumb|none|800px|Authentication Options]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
===Enforce TOTP Multi-Factor Authentication for Particular Roles=== | ===Enforce TOTP Multi-Factor Authentication for Particular Roles=== | ||
'''NOTE:''' Before enabling MFA for use with TOTP, all existing users with roles intended for TOTP must first scan their '''TOTP Secret Key''' or '''TOTP QR Code''' into an authenticator app. | '''NOTE:''' Before enabling MFA for use with TOTP, all existing users with roles intended for TOTP must first scan their '''TOTP Secret Key''' or '''TOTP QR Code''' into an authenticator app. | ||
| Line 63: | Line 39: | ||
When logging into the system for the first time after TOTP has been activated on the user's role, the user must first follow these steps: | When logging into the system for the first time after TOTP has been activated on the user's role, the user must first follow these steps: | ||
| − | :# For existing users: from the login page, enter your email and password as usual to log in. For new users: use the Activation Link to set a password, and submit. | + | :# For existing users: from the login page, enter your email and password as usual to log in. For new users: use the Activation Link to set a password, and submit. |
:# You will then be presented with the following screen: <br /> [[File:MFASetupTOTP.png|thumb|none|800px|TOTP Setup Page.]] | :# You will then be presented with the following screen: <br /> [[File:MFASetupTOTP.png|thumb|none|800px|TOTP Setup Page.]] | ||
:# Follow the instructions listed on the screen, starting by installing an authenticator app on your mobile device. | :# Follow the instructions listed on the screen, starting by installing an authenticator app on your mobile device. | ||
| Line 89: | Line 65: | ||
:# In the field '''Roles this role can reset TOTP for''', select the other roles that this role can reset TOTP on behalf of. <br /> [[Image:RolesTOTPReset.png|500px]] | :# In the field '''Roles this role can reset TOTP for''', select the other roles that this role can reset TOTP on behalf of. <br /> [[Image:RolesTOTPReset.png|500px]] | ||
:# Click '''Save''' when complete. | :# Click '''Save''' when complete. | ||
| + | |||
| + | ===Setting up Verification Codes for Email=== | ||
| + | The easiest way to set up MFA is through the email that was used for user registration and login. Be sure to follow the instructions carefully to avoid accidentally locking yourself or others out of their accounts. | ||
| + | |||
| + | # Go to '''Menu Icon''' > '''Global Settings''' > '''Security''' tab > '''Password and Activation Policies''' and then scroll down to the section marked '''Authentication Options'''. | ||
| + | # Toggle on '''Enable Multi-Factor Authentication'''. You will see additional settings displayed for different authentication methods. | ||
| + | # Under the '''Roles with Verification Code via SMS or Email''' setting, you will need to decide which roles need to be authenticated via a verification code sent through the email address used for login. Ensure that users assigned to this role have not opted out of receiving system emails. Click the '''Save''' button at the bottom of the page to activate changes.<br /> [[File:2022-11-ticket-139210-3.png|thumb|none|500px]] | ||
| + | |||
| + | |||
| + | ===Logging in with a Verification Code from Email=== | ||
| + | When a user has been assigned a role that requires a verification code, they can login using the following steps: | ||
| + | |||
| + | # When the user logs in using their email and password, they will be prompted to enter a verification code that was sent to their email. <br /> [[File:2022-11-ticket-139210-4.png|thumb|none|500px]] | ||
| + | # The user can check their email to copy the verification number. <br /> [[File:2022-11-ticket-139210-5.png|thumb|none|500px]] | ||
| + | # Enter the verification code into the field and then click '''Submit''' to finish authenticated login. | ||
| + | |||
| + | ===Setting up Verification Codes for SMS=== | ||
| + | In order for users to receive SMS messages, a SmartSimple administrator must first enable SMS services by going to '''Menu Icon''' > '''Global Settings''' > '''Communications''' tab > Toggle on '''Enable SMS Notification'''. Ensure that the target users have an active mobile number filled into this standard field. If the phone number field is empty, users will not be able to receive any SMS messages for login and may be locked out of their accounts once activated. | ||
| + | [[File:2022-11-ticket-139210-8.png|thumb|none|500px]] | ||
| + | |||
| + | ===Logging in with a Verification Codes for SMS=== | ||
| + | # When the user logs in, they will be presented with the option to receive a verification code via email (if available) or through SMS. The user can click '''Send Code by Text Message'''. <br /> [[File:2022-11-ticket-139210-6.png|thumb|none|500px]] | ||
| + | # The user can check their mobile messages, enter the code into the field, and then click '''Submit''' to finish authenticated login. <br /> [[File:2022-11-ticket-139210-7.png|thumb|none|500px]] | ||
| + | |||
| + | |||
=Settings Explained= | =Settings Explained= | ||
Revision as of 12:01, 11 January 2023
Contents
- 1 Overview
- 2 Configuration
- 2.1 Enforce TOTP Multi-Factor Authentication for Particular Roles
- 2.2 Logging in the First Time with TOTP
- 2.3 If the Mobile Device Associated with TOTP is Misplaced
- 2.4 Determining Which Roles Can Reset TOTP
- 2.5 Setting up Verification Codes for Email
- 2.6 Logging in with a Verification Code from Email
- 2.7 Setting up Verification Codes for SMS
- 2.8 Logging in with a Verification Codes for SMS
- 3 Settings Explained
- 4 See Also
Overview
Multi-Factor Authentication is a method of authentication in which a user is granted access to your SmartSimple Cloud system only after successfully presenting two or more pieces of evidence to an authentication mechanism.
The security impact of Multi-Factor Authentication (MFA) is that while a user might lose their authentication device or get tricked into sharing a password, the odds of both happening to a single user are dramatically reduced. Using MFA therefore enhances an organization's security by requiring users to identify themselves with more than their login credentials.
SmartSimple Cloud supports two ways of implementing Multi-Factor Authentication:
- Time-based One-Time Password (TOTP) via an authenticator app, which is more secure and suitable for users with increased access such as global administrators or internal staff
- Single Use Verification Code sent via email or SMS, which is better suited for external users or users who login infrequently
Configuration
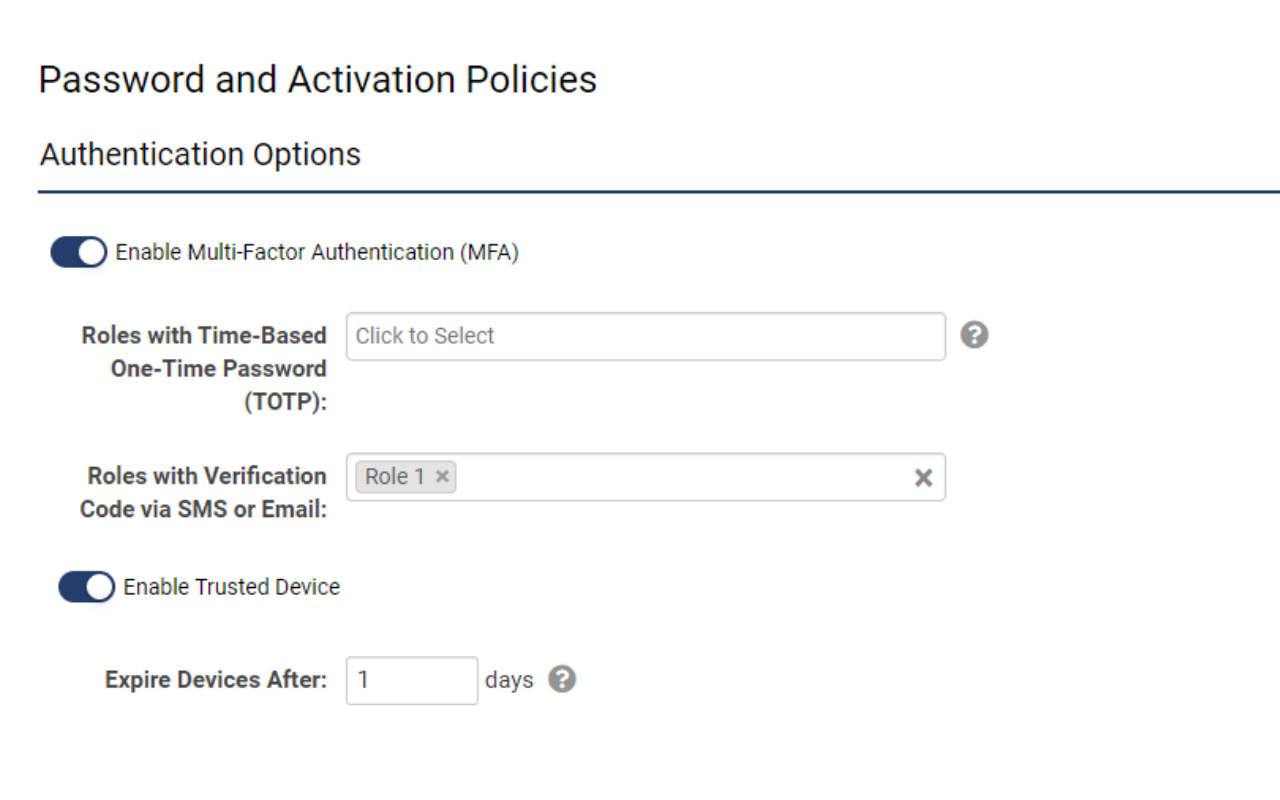
All settings related to multi-factor authentication are in a single location
- Navigate to Global Settings > Security > Password and Activation Policies
- Scroll to Authentication Options and toggle on Enable Multi-Factor Authentication
- Specify the roles that require authentication via TOTP and/or Verification Code
NOTE: If new roles are added to the system, the MFA configuration must also be updated
Enforce TOTP Multi-Factor Authentication for Particular Roles
NOTE: Before enabling MFA for use with TOTP, all existing users with roles intended for TOTP must first scan their TOTP Secret Key or TOTP QR Code into an authenticator app.
- In your SmartSimple instance (logged in as Global Admin) in the Configuration Menu (9-Square Grid Icon), select Global Settings.
- Select the Security Tab from the Global Settings.
- Click Password and Activation Policies.
- Under “Authentication Options”, toggle on Enable Multi-Factor Authentication (MFA).
- In the setting Roles with Time-Based One-Time Password (TOTP) include the roles that you will be adding 2-Factor Authentication for. Note that the existing users in these roles must first scan the QR Code on their mobile device before this setting should be toggled on.
- Toggle on Enable Trusted Device if you would like users to be able to bypass entering a code for a time period after the code has been successfully entered. If enabled, also enter the time period that the 2-Factor Authentication will be bypassed for trusted users.
- Scroll to the bottom of the page and click Save.
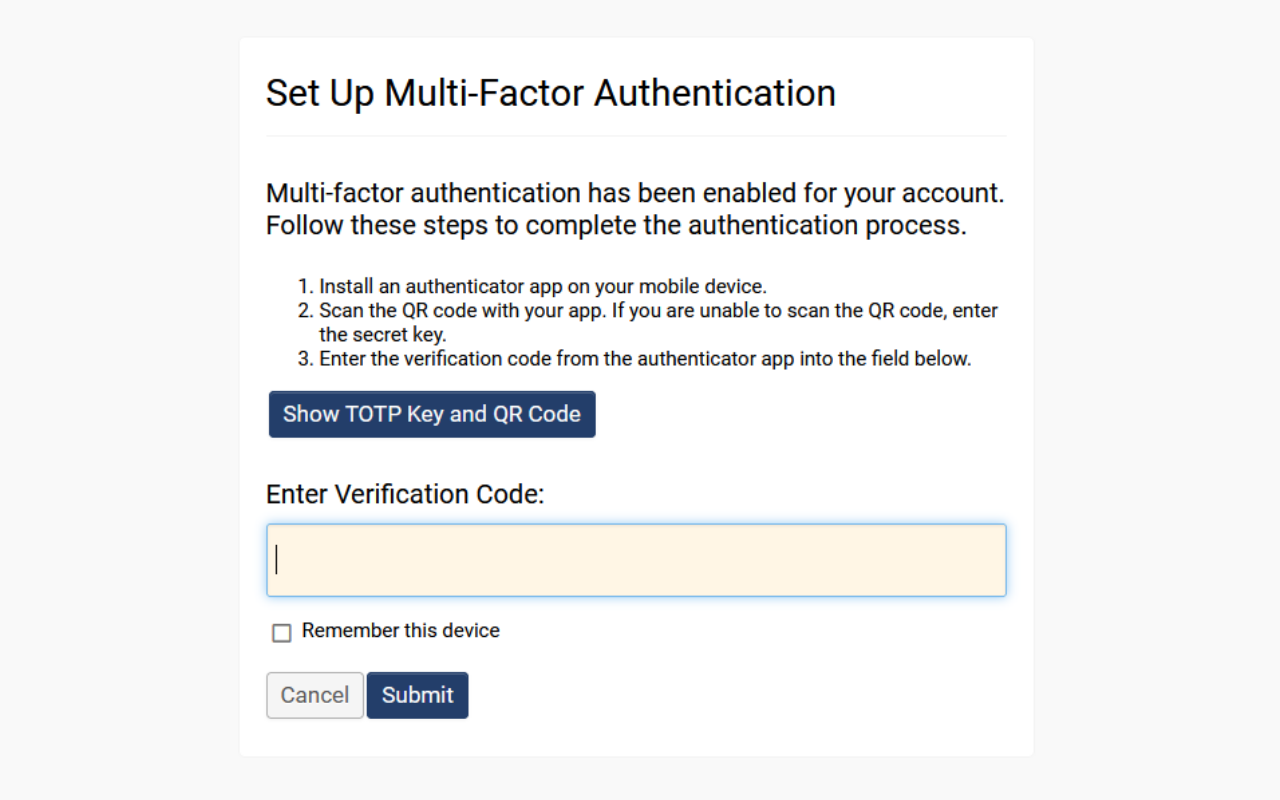
- To test your MFA, log out of your account, and then log back in. You should now see a page following login called “Set Up Multi-Factor Authentication.” Follow the instructions in the following section to set up TOTP Multi-Factor Authentication.
- In your SmartSimple instance (logged in as Global Admin) in the Configuration Menu (9-Square Grid Icon), select Global Settings.
Logging in the First Time with TOTP
In order to use TOTP effectively, users must first download an authenticator application onto their mobile devices. Popular authentication apps include Google Authenticator, Microsoft Authenticator, or 2FAS. When logging into the system for the first time after TOTP has been activated on the user's role, the user must first follow these steps:
- For existing users: from the login page, enter your email and password as usual to log in. For new users: use the Activation Link to set a password, and submit.
- You will then be presented with the following screen:
- Follow the instructions listed on the screen, starting by installing an authenticator app on your mobile device.
- On your mobile device, open the authenticator app and select “Add new device” or similar. Then select “Scan QR Code” or similar.
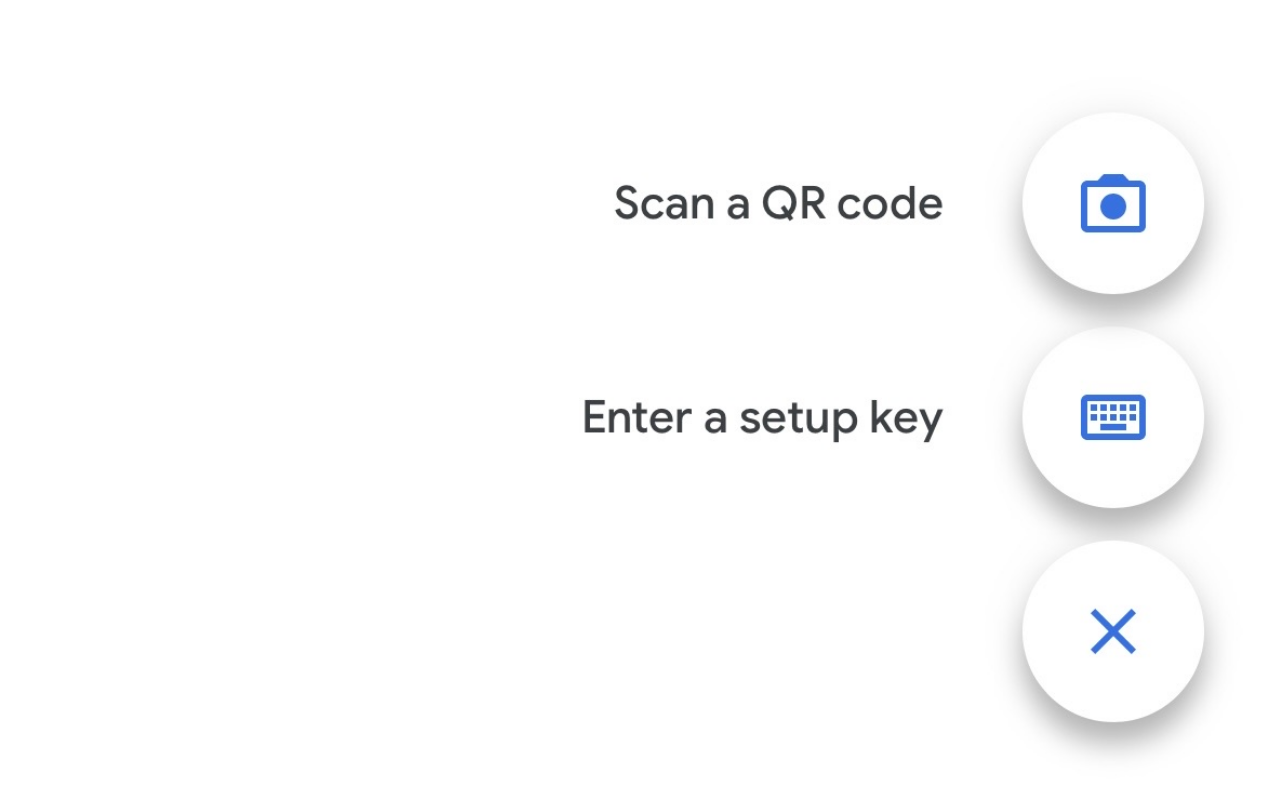
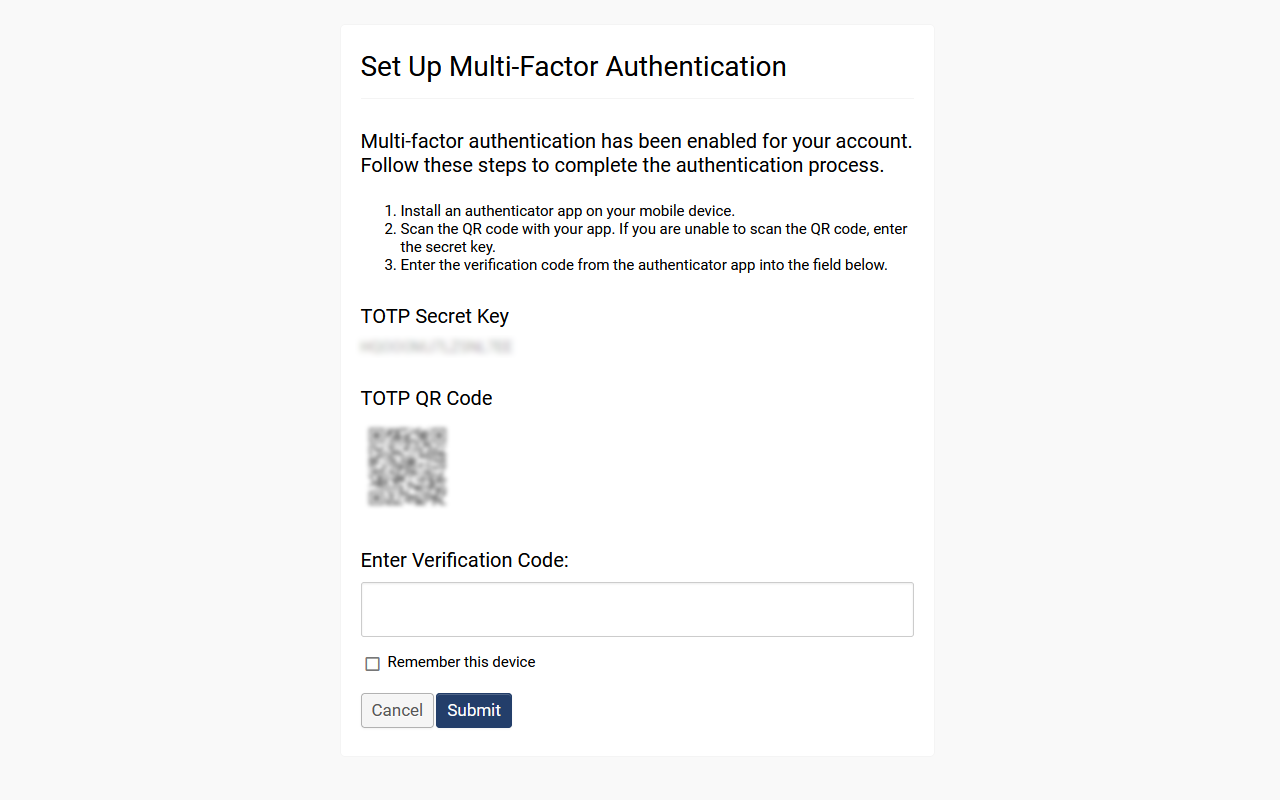
- Clicking the button "Show TOTP Key and QR Code" reveals the QR and secret code used with an authentication app.
- After scanning the QR Code or entering the TOTP Secret Key in your Authenticator app, a new device should be added to your list. Alternatively, you could also use the TOTP Secret Key as opposed to the TOTP QR Code.
- Next, enter the TOTP Verification Code in the modal window.
- Press Submit when done.
If the Mobile Device Associated with TOTP is Misplaced
NOTE: If a mobile device associated with TOTP is misplaced, TOTP must be reset by a Global Admin, or a user in a role with Role can reset TOTP for permissions in the role's setting page (More information detailed in the following section).
In the case of a user's device being misplaced, the following steps will allow an internal user in the roles listed above to reset a user's TOTP:
- First, navigate to the user's profile who wishes to have TOTP credentials reset.
- Next, from the Actions dropdown, select Edit Roles and Access.
- In the following modal window, select the button labeled Reset TOTP.
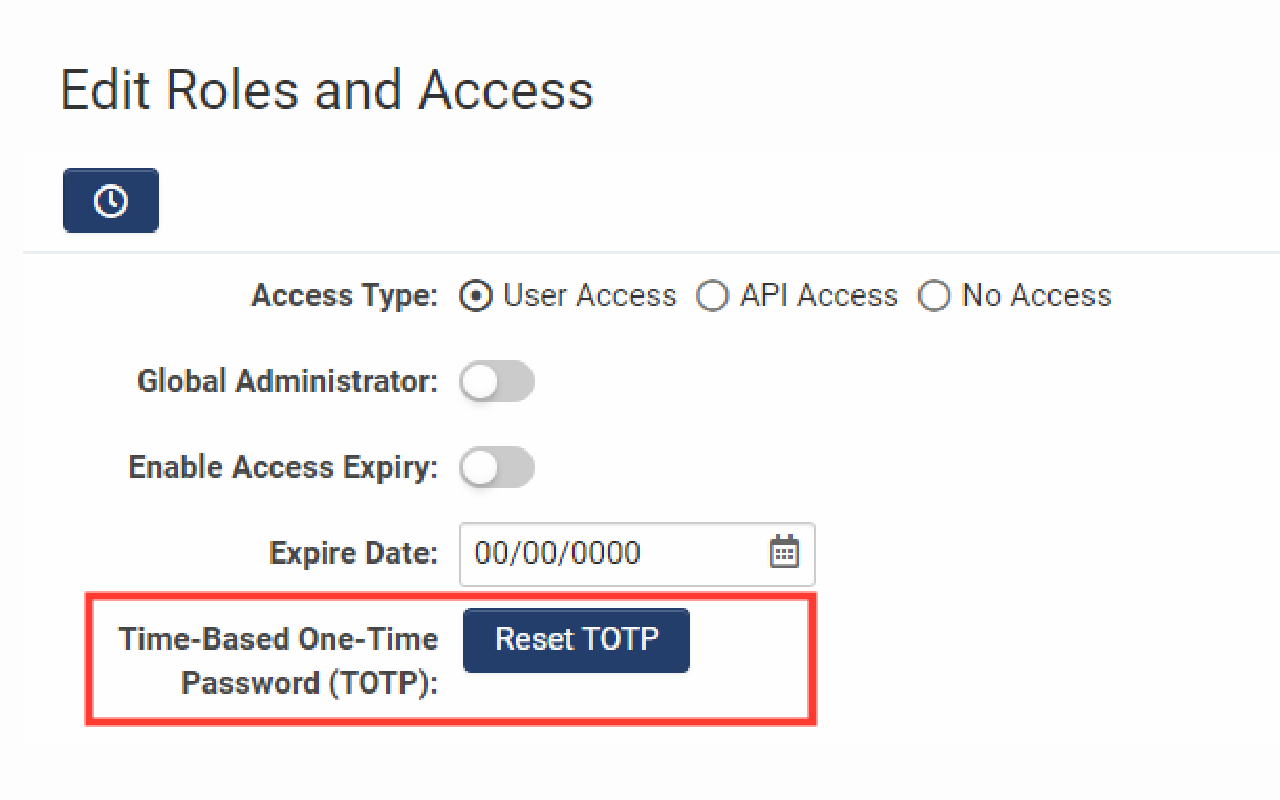
- The user may now login as normal, following the prompts on the subsequent Set Up Multi-Factor Authentication screen.
Determining Which Roles Can Reset TOTP
- In your SmartSimple instance (logged in as Global Admin) in the Configuration Menu (9-Square Grid Icon), select Global Settings.

- Select the Users Tab from the Global Settings.
- Click Roles.
- Edit the role that you would like to grant the ability to reset TOTP on behalf of other users. For security best practices, this role should be an internal role only.
- Select the Permissions tab.
- In the field Roles this role can reset TOTP for, select the other roles that this role can reset TOTP on behalf of.
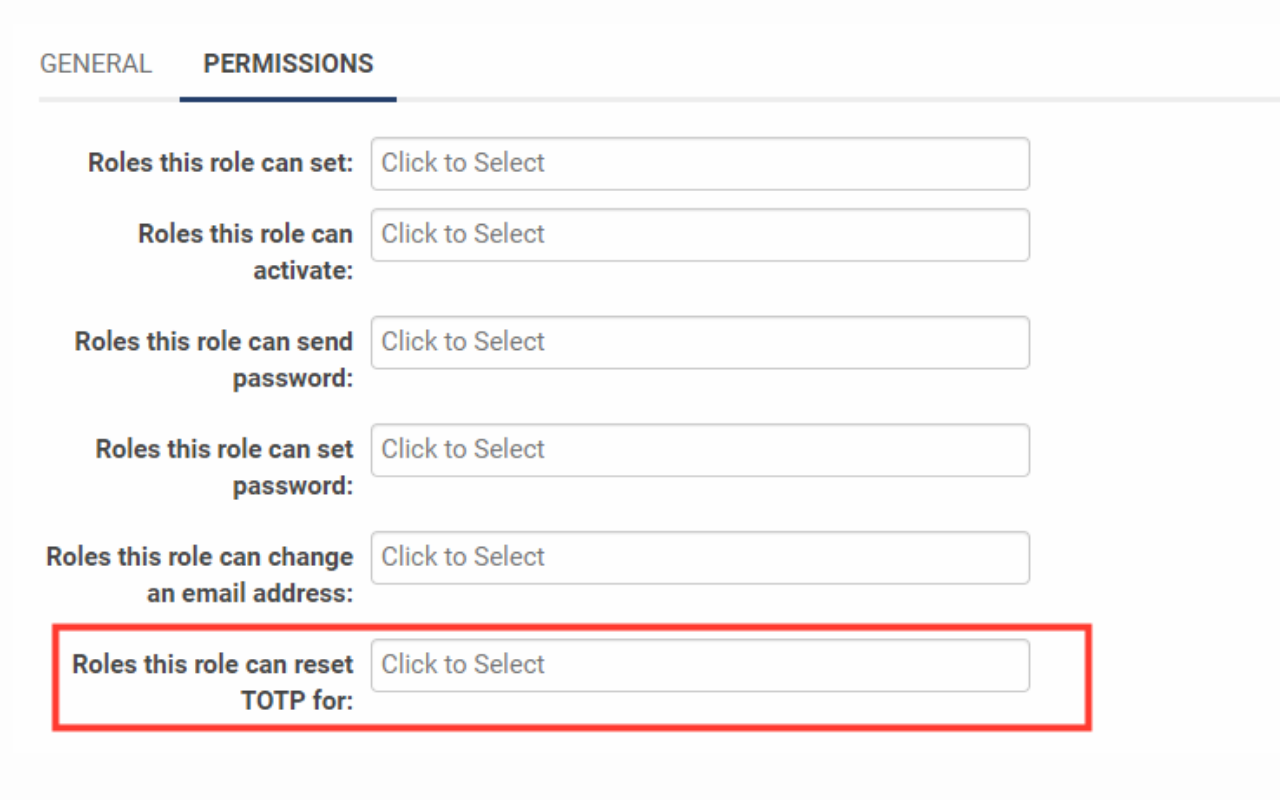
- Click Save when complete.
- In your SmartSimple instance (logged in as Global Admin) in the Configuration Menu (9-Square Grid Icon), select Global Settings.
Setting up Verification Codes for Email
The easiest way to set up MFA is through the email that was used for user registration and login. Be sure to follow the instructions carefully to avoid accidentally locking yourself or others out of their accounts.
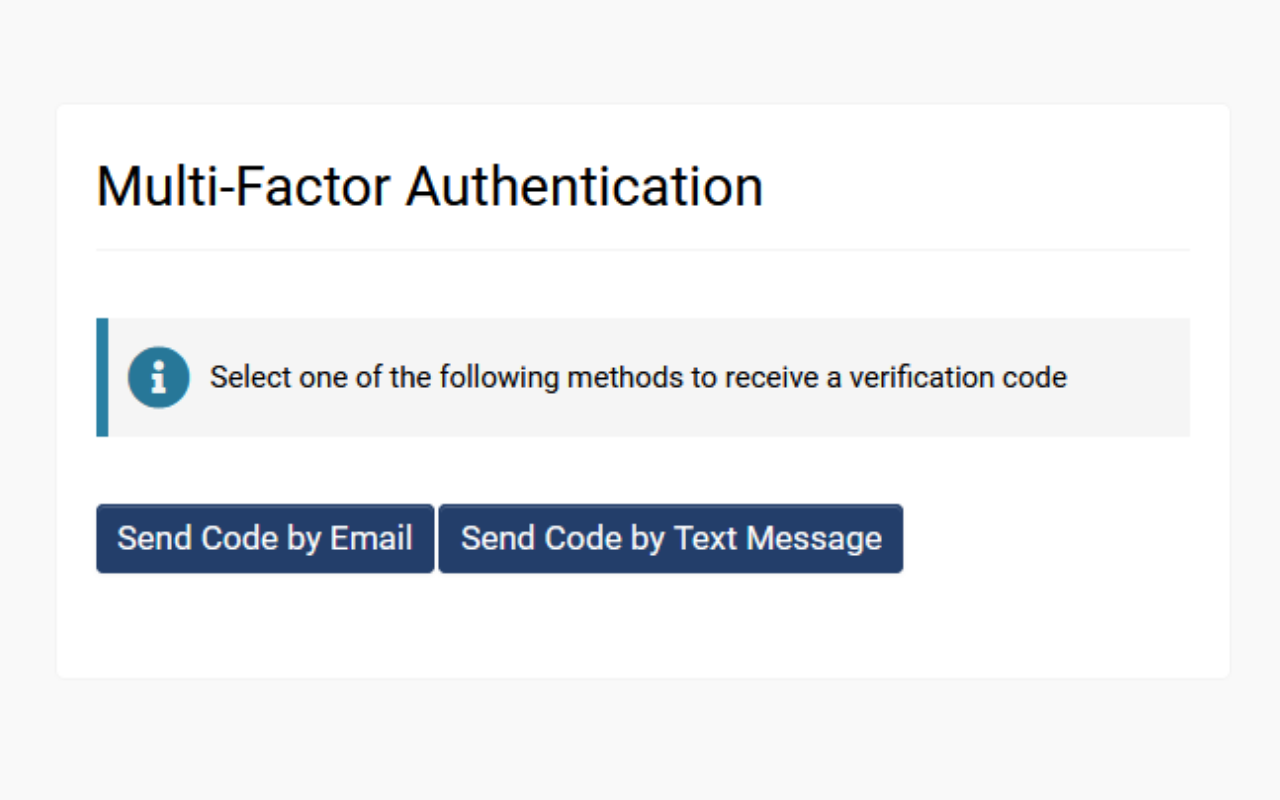
- Go to Menu Icon > Global Settings > Security tab > Password and Activation Policies and then scroll down to the section marked Authentication Options.
- Toggle on Enable Multi-Factor Authentication. You will see additional settings displayed for different authentication methods.
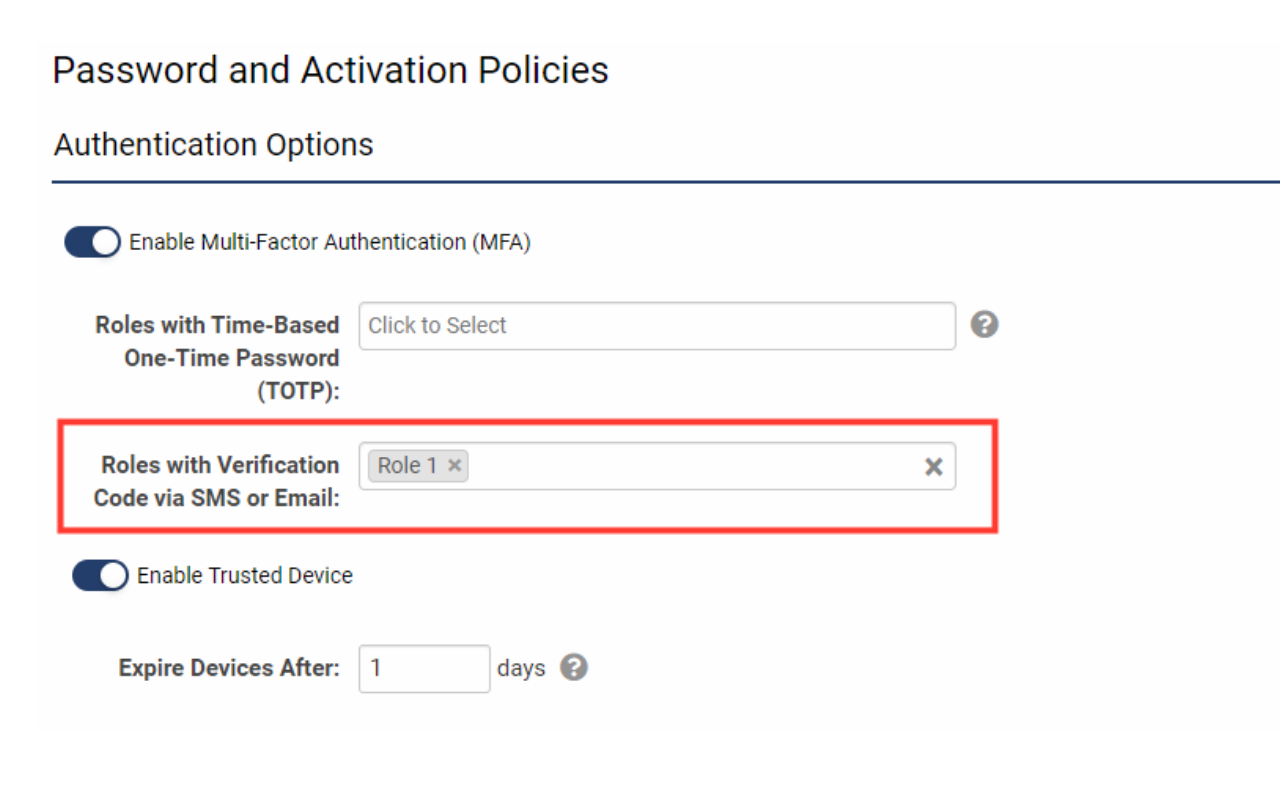
- Under the Roles with Verification Code via SMS or Email setting, you will need to decide which roles need to be authenticated via a verification code sent through the email address used for login. Ensure that users assigned to this role have not opted out of receiving system emails. Click the Save button at the bottom of the page to activate changes.
Logging in with a Verification Code from Email
When a user has been assigned a role that requires a verification code, they can login using the following steps:
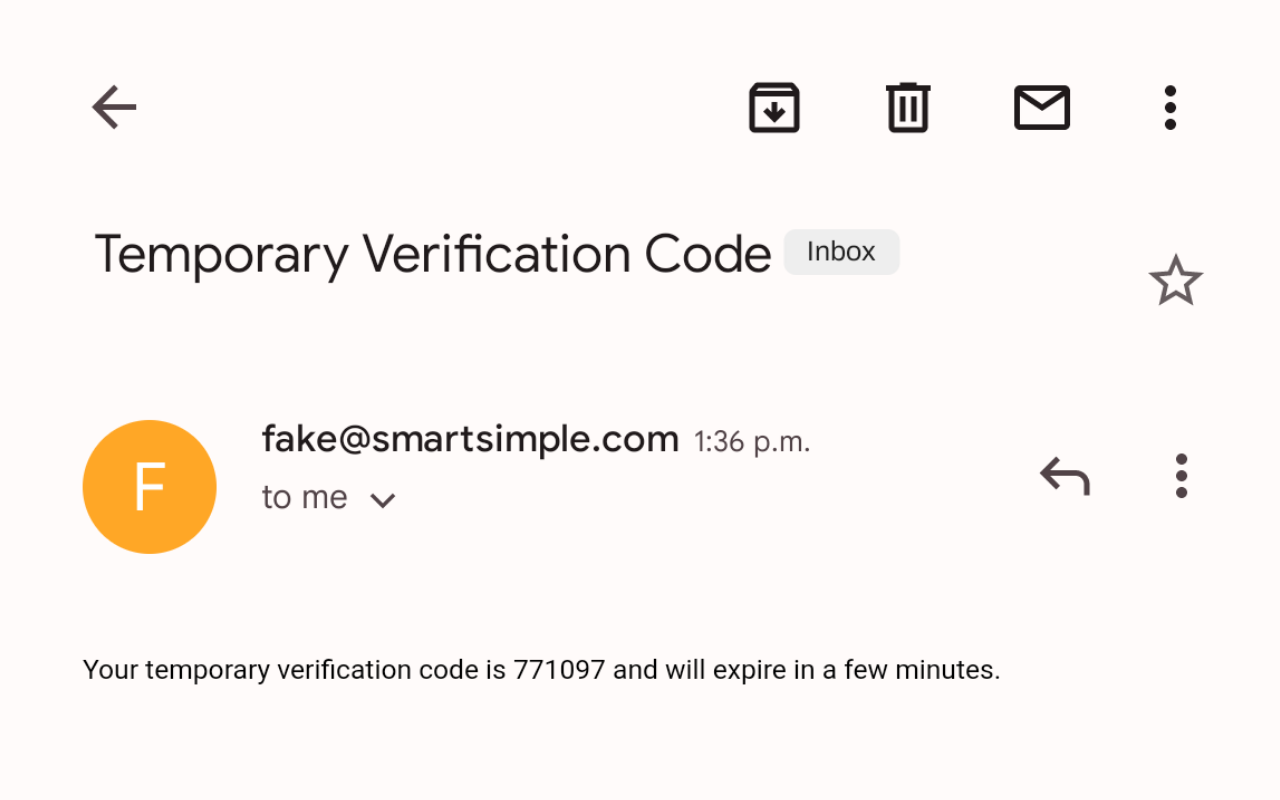
- When the user logs in using their email and password, they will be prompted to enter a verification code that was sent to their email.
- The user can check their email to copy the verification number.
- Enter the verification code into the field and then click Submit to finish authenticated login.
Setting up Verification Codes for SMS
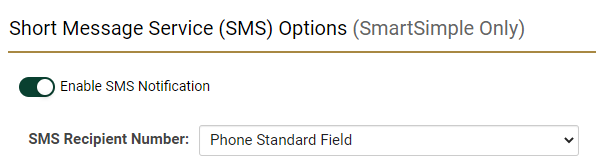
In order for users to receive SMS messages, a SmartSimple administrator must first enable SMS services by going to Menu Icon > Global Settings > Communications tab > Toggle on Enable SMS Notification. Ensure that the target users have an active mobile number filled into this standard field. If the phone number field is empty, users will not be able to receive any SMS messages for login and may be locked out of their accounts once activated.
Logging in with a Verification Codes for SMS
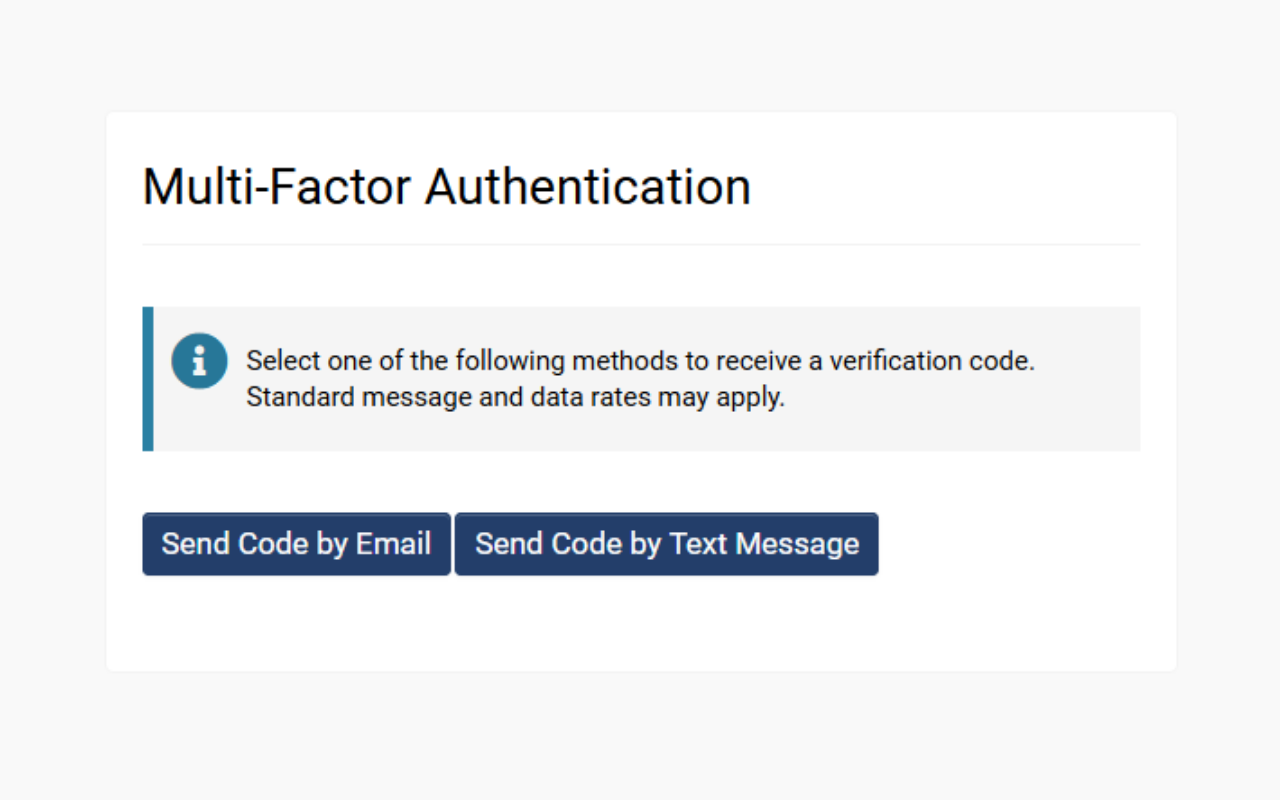
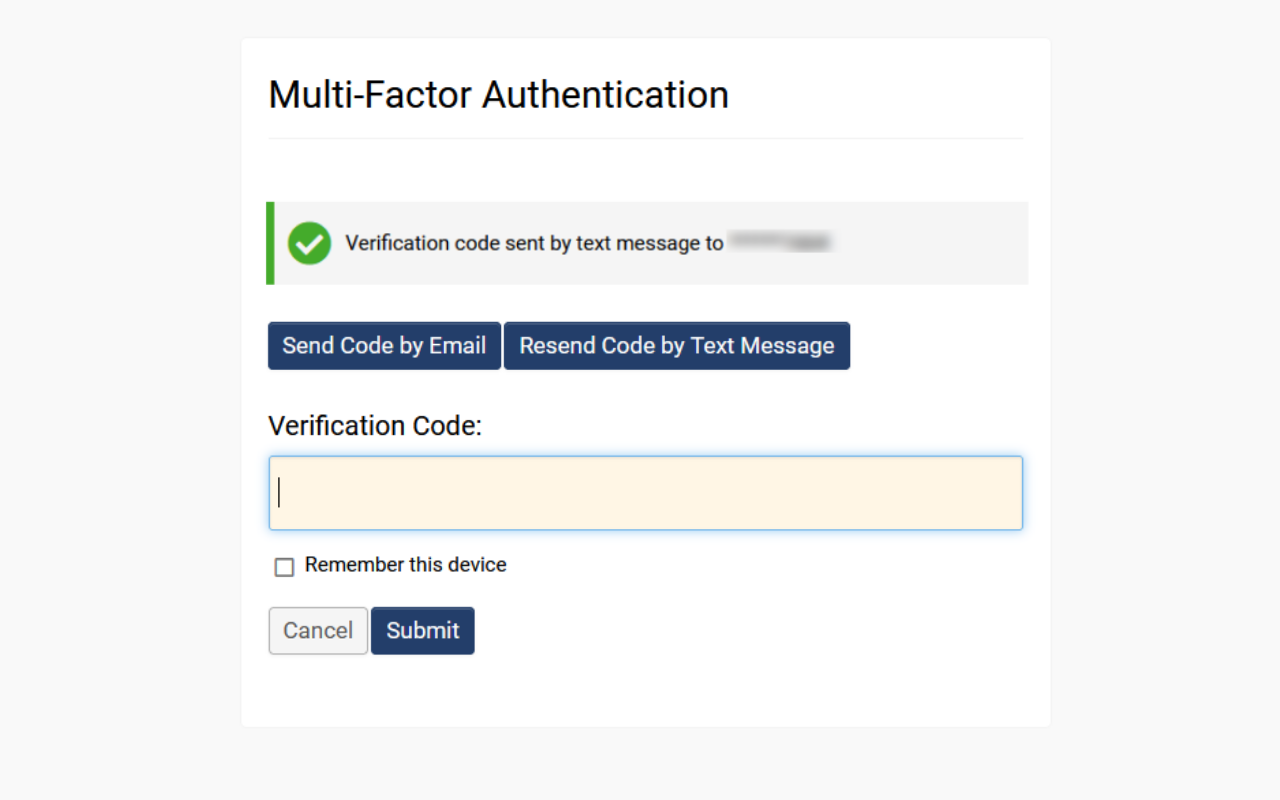
- When the user logs in, they will be presented with the option to receive a verification code via email (if available) or through SMS. The user can click Send Code by Text Message.
- The user can check their mobile messages, enter the code into the field, and then click Submit to finish authenticated login.
Settings Explained
|
Setting |
Description |
|
Enable Multi-Factor Authentication |
Enables MFA for the entire instance but does not have any impact unless user roles are specified. |
|
Roles with Time-based One-time Password (TOTP) |
Associates one or more roles with authentication proven through an authenticator app such as Google or Microsoft Authenticator. |
|
Roles with Verification Code via SMS or Email |
Associates one or more roles with authentication proved through either email or an SMS message. The user can choose at the point of verification to receive an email containing the one-time-code or an SMS message containing the one-time code. SMS must be enabled by SmartSimple and will incur an additional cost. Please speak to your account manager for more information. |
|
Enable Trusted Device |
This option is used to enable the trusted device feature. If this option is selected then every user (via their role) associated with MFA will not be prompted every time they attempt to log into the system. |
|
Trusted Device Expiry |
Sets the frequency of the MFA prompt, based on the number of days specified. If the number is set to one, the user will be prompted every day for an MFA verification code, if set to five then the user will be prompted every five days. |