Difference between revisions of "Multi-Factor Authentication"
Ann Vincent (talk | contribs) m |
Bankole Oni (talk | contribs) (→No summary) |
||
| Line 29: | Line 29: | ||
'''Settings Explained''' | '''Settings Explained''' | ||
| − | {| style="border-color: # | + | {| style="border-color: #000000;" |
|- | |- | ||
|| | || | ||
| Line 39: | Line 39: | ||
|- | |- | ||
|| | || | ||
| − | Enable Multi-Factor Authentication | + | '''Enable Multi-Factor Authentication''' |
|| | || | ||
| Line 46: | Line 46: | ||
|- | |- | ||
|| | || | ||
| − | Roles with Time-based One-time Password (TOTP) | + | '''Roles with Time-based One-time Password (TOTP)''' |
|| | || | ||
| Line 53: | Line 53: | ||
|- | |- | ||
|| | || | ||
| − | Roles with Verification Code via SMS or Email | + | '''Roles with Verification Code via SMS or Email''' |
| style="border-color: #000000;"| | | style="border-color: #000000;"| | ||
| Line 65: | Line 65: | ||
|- | |- | ||
|| | || | ||
| − | Enable Trusted Device | + | '''Enable Trusted Device''' |
|| | || | ||
| Line 74: | Line 74: | ||
|- | |- | ||
|| | || | ||
| − | Trusted Device Expiry | + | '''Trusted Device Expiry''' |
|| | || | ||
Revision as of 10:55, 8 November 2022
Overview
Multi-Factor Authentication is a method of authentication in which a user is granted access to your SmartSimple Cloud system only after successfully presenting two or more pieces of evidence to an authentication mechanism.
The security impact of Multi-Factor Authentication (MFA) is that while a user may lose an access card or get duped into sharing a password, the odds of both happening to a single user are dramatically reduced. Using MFA therefore enhances an organization's ability to ensure that no one is using illegitimate means to gain access.
SmartSimple Cloud supports two different approaches to Multi-Factor Authentication:
Time-based One-Time Password (TOTP) - this technique uses an authentication app that is installed on a mobile phone or other personal device.
Verification Code – a single use code sent by either Email or SMS to a user specified email address or phone number
Configuration
All settings related to Multi-Factor Authentication are in a single location
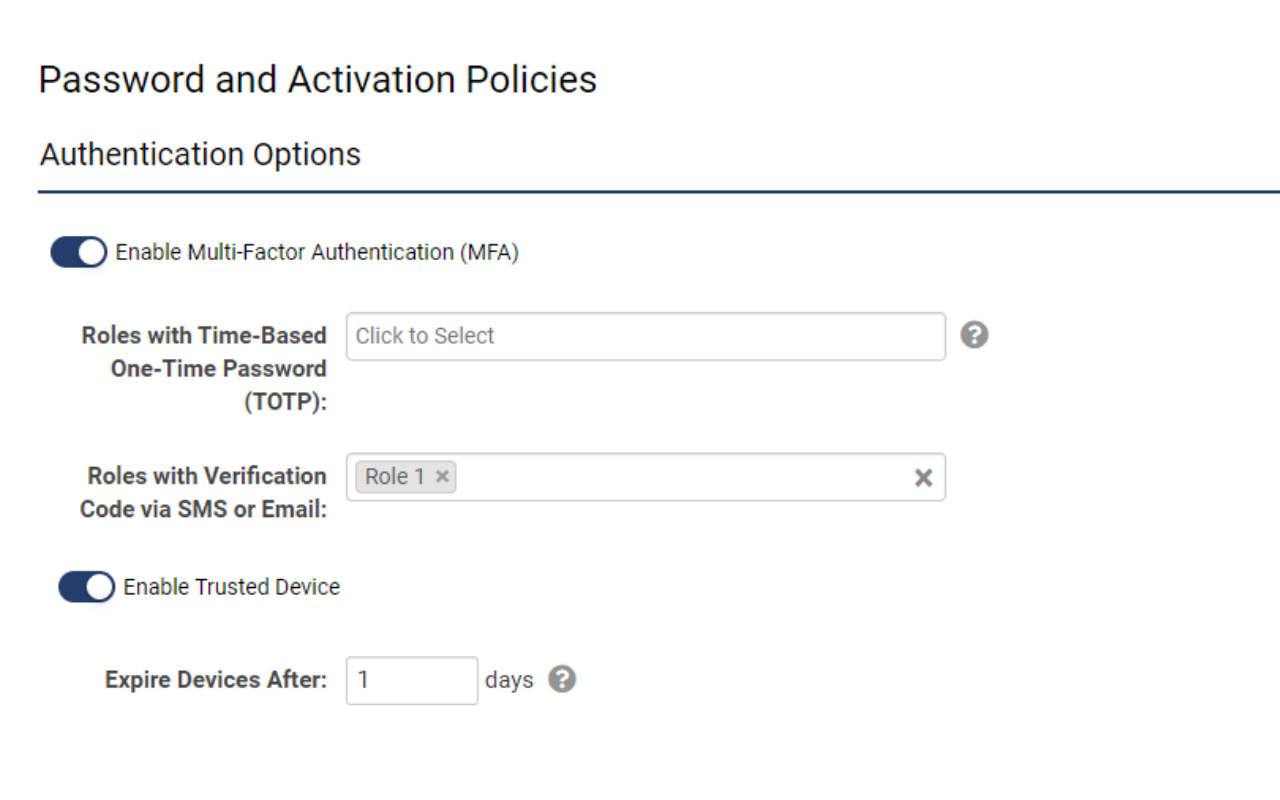
- Navigate to Global Settings > Security > Password and Activation Policies.
- Scroll to Authentication Options and toggle on Enable Multi-Factor Authentication
- Specify the roles that require authentication via TOTP and/or Verification Code
NOTE: If new roles are added to the system, the MFA configuration must also be updated
Settings Explained
|
Setting |
Description |
|
Enable Multi-Factor Authentication |
Enables MFA for the entire instance but does not have any impact unless user roles are specified. |
|
Roles with Time-based One-time Password (TOTP) |
Associates one or more roles with authentication proven through an authenticator App such as Google or Microsoft Authenticator. |
|
Roles with Verification Code via SMS or Email |
Associates one or more roles with authentication proved through either Email or an SMS message. The user can choose at the point of verification to receive an email containing the one-time-code or an SMS message containing the one-time code.
|
|
Enable Trusted Device |
This option is used to enable the trusted device feature. If this option is selected then every user (via their role) associated with MFA will not be prompted every time they attempt to log into the system. |
|
Trusted Device Expiry |
Sets the frequency of the MFA prompt, based on the number of days specified. If the number is set to one, the user will be prompted every day for an MFA verification code, if set to five then the user will be prompted every five days. |